Sharon Nelson and John Simek, of Sensei Enterprises, a digital forensics and information security firm, host a monthly podcast called Digital Detectives on the Legal Talk Network. They discuss digital forensics, e-discovery, and information security issues. Nelson and Simek invite digital forensic and security experts to enlighten listeners on the latest technology, cyber threats, and necessary security measures to keep online data secure.
For the March 2017 episode their guest was Charles Patterson, founder and president of Exec Security TSCM. They discussed TSCM and how security sweeps can help ensure privacy for lawyers and their clients.
You can read the transcription of this interview below.
Sharon: Today on Digital Detectives our topic is “electronic security sweeps for law firms and their clients”.
We are delighted to welcome as today’s guest, Charles Patterson, the founder and president of Exec Security TSCM, specializing in Technical Surveillance Countermeasures, often referred to as “electronic bug sweeps”. They have been providing security sweeps for major corporations and high profile clientele for over twenty years. Charles began his security career in 1978 working in executive protection and technical security services traveling throughout the United States and over forty different countries. During that time he gained extensive experience with many different technologies including two-way radio, telecom, audio systems, video surveillance, and many others, and that led him to start his own business in 1995, specializing in TSCM. Exec Security is one of the few full time professional providers of electronic TSCM sweeps in the United States serving major corporations, attorneys, and private investigation firms throughout the US and the world.
John: Thanks for joining us today, Charles.
Charles: Thank you for having me.
Sharon: I have to tell you Charles that when I first read the acronym TSCM, I went “what is that?”, so I was happy to eventually see it spelled out. But I am guessing that many of our listeners do not know what “technical surveillance countermeasures” actually means in the real world. So can you help them to understand?
Charles: Sure, the initials are easy to mix up. I hear people all the time going “T-C-S-M” or just mixing the letters up, but that happens with acronyms all the time. If you break it apart, it is “technical surveillance” … and “countermeasures”. So it’s about how to protect yourself against technical surveillance.
Technical surveillance can come from a lot of different things. It could be radio transmitters, “bugging devices”, hidden microphones, miniature recorders, covert video cameras are also a big problem. Other concerns include wiretaps and communications interception; and that can be telephone interception but it could also be attacks against other things such as intercoms, paging systems, conference equipment, any type of audio or video transmission or any other loss of information through technical means. That’s what we want to protect against. That’s where the countermeasures come in.
It not exactly like the movies. A lot of time you may see in a movie somebody is waving around a little black box with an antenna and if it beeps or lights up they think they found a bug, but there really is a lot more than that. Detection techniques include radio signal analysis, that’s part of it, using spectrum analyzers and other radio equipment. Thermal imaging has become very useful tool in recent years. Electronic device detection is used for detecting various types of electronic components. And of course, telecom, data, and wiring inspection is necessary. A major part of every sweep is the physical inspection as well, where we really take a close look at any area that might be concealing a threat, whether that means looking under furniture or even in ceilings and air vents.
John: Charles, I’m glad to hear that it’s not like television. I get the same thing doing forensics work. I don’t watch CSI anymore. So I’m glad to hear that. Can you discuss how TSCM is related to cyber security?
Charles: Sure. I started listening to your podcast a couple of years ago because you are covering a lot of the important digital concerns that people face today. Cyber is such a big concern. The threat is big and the risk is big as well. But there are some areas of information security that may not quite be covered fully by cyber security and they may not be covered by other aspects of security like physical security. In Wifi networks, for instance, there could be rogue access points that may not be detected or noticed by the IT department. They may be protecting you from internet attacks with a good firewall but not always seeing what is happening within your network. You may be doing a good job protecting the network from the outside, while an insider may come along and install a rogue device that could go undetected for quite a while.
Also within the wiring in the physical layer of the network it’s possible to install in an ethernet tap that will physically tap into a data line. Also, there are spare wires in every ethernet jack that may need to be checked. The spare pairs of wires have been known to be used for connecting to a microphone. We even found a microphone built inside an RJ45 ethernet plug, using a spare pair. So this allowed whoever was at the other end, whether it was at a patch panel or somewhere down the line, to tap into that wire and listen to the room conversations.

Miniature microphone was concealed in an ethernet plug.
Sharon: So why do companies need to have these types of sweeps done?
Charles: We consider three categories for why people need sweeps. When people call us it is usually for one of these three reasons.
–Incident Response–
One is incident response. Somehow the client has detected that information has been leaked or they suspect that information has been leaked. It could be that some confidential information was found online and they thought “how did that information get out?”
Another concern might be if there was a break-in at the company. It may appear as if someone was just trying to commit a theft or a robbery but perhaps that was a cover for something else, maybe they were trying to plant an eavesdropping device.
Or the company may just be suspicious about an employee or even an executive who was just fired. They may say “we need to find out – was any spying going on?”, or was there any eavesdropping device that they may have left behind?
–Regular Sweeps for Precautionary Security–
Another category is just regular security concerns. Many corporations have electronic sweeps done periodically, where there has been no specific threat, but we will come in and do a sweep just to make sure security is maintained. Quarterly is recommended but it could be semi-annually, depending on the concerns.
You might compare it to having a fire inspection done. You don’t think there is going to be a fire, but you want have someone professional check to make sure there are no threats present.
–Special Events–
Then there is a third category when there is a serious or significant upcoming event, perhaps a board meeting or some other meeting or conference. Often they may be held at hotels where we are called in in advance to check out the boardroom, the conference room, or meeting room, to make sure that it is secure and make sure that it stays secure for the duration of the meeting.

Hotel and conference center meeting rooms need to be secure.
It is important to understand the risk that is involved, too. The loss of confidential information will translate into loss of dollars as well. There could be corporate strategy, details of mergers and acquisitions, stock offerings, personnel changes, even executive schedules that need to be protected. I used to work in executive protection and one of the things that really needed to be kept secret was what was happening in the executive’s schedule, because a leak of that information could open them up to other types of physical attack.
And then it is also important to understand who may be a possible threat. Who would your enemy be? Is it a competitor, a disgruntled employee, or maybe an executive who is just jealous or looking advance his position? Or possibly a legal adversary? Legal problems are a big concern. All these things together will prompt a company to schedule a sweep.
John: Now Charles, who are the typical clients?
Charles: Many times those who call us, as I mentioned, may be calling for an incident response, one of the first things they say is “I never thought we would be needing this, but…” and then they go on to explain some sort of incident that occurred.
–Corporate Security, Legal Counsel–
Sometimes we are contacted by corporate security. We work closely with the corporate security departments of a number of different major corporations. They keep in touch with the legal department and are called upon to handle this type of security concern.
–Attorneys–
We are also contacted directly by attorneys, sometimes it may be along with a private investigator. There may be a concern for one of the attorney’s clients where they realize that the nature of the lawsuit, the nature of the concern, is serious enough that a sweep is in order and we will take a good look at their facility.
–Private Investigators–
There are a number of good private investigation firms, and many of them may offer sweeps themselves, but often they are not equipped to do a full, thorough job. We work closely with a number of these firms so that when there is a serious need they can call us in to help handle the situation professionally.
Whenever we get a call directly from an individual client, one of the first questions we always ask is “have you been in touch with your attorney”? This is because they are going to need their attorney one way or another. If we do find an eavesdropping device, they are going to need their attorney to help take the next steps. And even if we come and we don’t find a suspicious device, the client still has issues to face and they will need the attorney to try to understand the situation. Why did they suspect the problem in the first place? Was information leaked some other way? Maybe it was by word of mouth.
No one wants to admit that they blabbed something. Sometimes we have been called in and the security director says, “we want to make sure there are no bugs here, the bosses think there might be, but just between you and me, I think somebody just talked to much.” As a matter of security, we will go ahead and check the facility for them.
Sharon: You’ve mentioned a couple of ideas of why lawyers might request a sweep. Are there others?
Charles: Yes, as we said, law firms may need sweeps for their own offices. Is there some major litigation going on, a major case that is significant enough that it demands security? In that case you would want your own conference rooms or offices swept to be sure that they are secure.
Or perhaps, your firm is always dealing with such cases so you may need sweeps done on a regular basis. We know some larger law firms have their own TSCM teams providing sweeps at their offices around the country and even around the world inspecting the conference rooms in those locations.
Other times it may just be a case comes up where they feel the opposing counsel may have too much information. You want to be sure you are doing your fiduciary responsibility, making sure that everything is as secure as possible for your clients.
Much of the concern is at the corporate level, so for legal counsel for a corporation, their own offices may be of concern but it may be other areas within the corporation that they realize need regular sweeps.
And again as I mentioned, if there was a break-in or perhaps if an executive was recently fired, the attorney should know if there was any suspicious activity involved or other reason for concern. And then of course there are personal cases, matrimonial, even inheritance cases that may need attention.
We were called in for a case where a major family-owned company was going through some changes. One brother was being removed from his position and was going to work for the competition. No one seemed to like or trust him. They were very concerned about communication leaks and what information might be changing hands.

John: Charles, can you tell our listeners how are sweeps actually performed? Can you tell us something about the equipment, the tools, techniques, those kinds of things including the things you might find in spy shops or on eBay. I might want to put some of those on my Christmas list.
Charles: There are a number of tools available but it’s necessary to understand what a tool does. As I mentioned there are small devices that you can buy online that will detect radio signals, and it may vibrate or it beeps when it is near a signal. But it is important to realize that are radio signals everywhere today. There are radio signals coming from your stereo system, signals coming from your computer, from your phone, even lighting and room occupancy sensors, all kinds of things. So a small little RF detector that is very generic may not be able to discern what type of signal you are finding.
In many environments it may be overwhelmed and would probably beep or vibrate constantly. We have much more advanced radio analysis equipment. We use laboratory grade spectrum analyzers that can connect to a computer for logging and processing data. It can run traces and detect signals throughout an entire area showing what frequency the signals are at, what the waveforms look like, and we can start to analyze it. Where is it coming from? Was this signal present the last time we swept here? We can then track it down with direction finding techniques if it is suspicious.
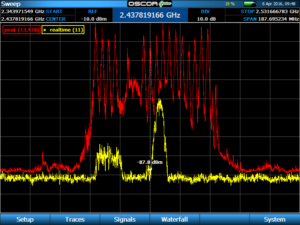
Radio signals need to be analyzed in detail.
So the radio signals are very important, and we look closely at that. We also use Thermal Imaging. Electronics, when active, when powered up, will generate heat. Thermal Imaging is particularly good for finding covert cameras. Small video cameras typically generate a lot of heat, enough that it could be spotted even if it was behind a ceiling tile in a drop ceiling, for instance. From standing on the floor and scanning the ceiling with a thermal imager you would be able to notice that there was a hot spot, and you would know that is something you need to check out.

Thermal Imaging reveals heat from electronic eavesdropping devices.
We use, also, a device called a non-linear junction detector. It’s another one of those long words that often uses initials, NLJD. Basically what it does is detect electronic components, such as diodes, transistors, and chips, even if they are not active. Even if the circuit is not turned on, even if it is not transmitting, the NLJD, the non-linear junction detector, has a way of detecting that there is an electronic component present.
For instance a device could be hidden in a book or other object. Particularly consider a law library. There are so many books that to go through each one manually could take forever. So this is a very helpful device that we use. That is one you might notice if you watch a movie with the Secret Service doing a sweep and it looks like there is a guy with a metal detector going up and down the wall with it. That’s the non-linear junction detector.
And of course, we have to look at wiring as well. Telecom and data wiring; and we will look into the outlets. We check wiring with what is called a TDR, a Time Domain Reflectometer. The TDR is sort of like a radar for wires. It will send a signal down a pair of wires and by analyzing the reflection coming back it can tell you if there are any anomalies and how far along the wire they may be located. Is there a device, a short circuit, or a splice or wiretap along the way?
There are a lot of different techniques like this that are used. And as I mentioned, the physical inspection is one of the most important parts of the sweep; that is where many devices are finally uncovered. Even if a device is not found, there may be traces of something left behind. We may find a little bit of duct tape stuck under a table for instance where a device was hidden.

Non-Linear Junction Detector, NLJD, locates electronic components.
This happened for one client. We were sweeping their conference room with a very large conference table. Underneath, in the very center of the table, a piece of cardboard was stapled to the wood, forming a small shelf. It was clearly done in an amateur manner by someone in a hurry. This made the perfect place to hide a recording device. A recording device was not there at the time of our sweep. The person doing the eavesdropping would enter the room ahead of a meeting, crawl under the table and leave a recorder on this shelf he had made, then retrieve the device later. So the recorder was not there when we did the sweep, but we did find the evidence that was left behind and the client knew this was one way that information was getting out. In a situation like this, they could check security video recordings to look for suspicious activity before or after a meeting.
There is limitation with many of the tools you may find online, but it’s a matter of understanding what the tool does and how then how to use it effectively. It’s kind of like, for instance, if someone said, “what’s the best screwdriver to fix my car”? Well, a screwdriver is one tool. The screwdriver is not going to let you solve every problem, but you certainly may use it. That’s the way a lot of the online tools are.

Crude shelf for eavesdropping device placed under conference table.
Sharon: Sounds like there are a lot of tools and it sounds like there is a lot to be found. So I’m listening to you, Charles, and I’m hearing about crawling under tables, and little cardboard shelves, it sounds like this might be quite the process in an office of any size. How much time would it take to do a sweep?
Charles: It can vary depending on the size of the area and what’s involved. Typically when we’re hired for a job we are looking at taking about four or five hours. That may include three or four offices and a conference room, and in some cases it will depend on how many people we bring with us on the sweep team. If we need to inspect a large area we may bring in a few extra technicians on the job.
There is a lot of tediousness to the work. Sometimes the client has unrealistic expectations, again they have watched sweeps in movies, and think we’re going to come in and be done in a short amount of time. They may even say, “well the last guy that was here, all he did was walk around and wave this antenna thing and he was done in less than an hour.” We have to tell them, “no, it’s not quite like that, we’re going to be here for three, four, five hours or more”. And then the client may wish they had brought a book to read, because they are going to have to sit around with us for that time.
Sharon: I’ll bet that’s true.
Charles: Yes, but at the same time we will have clients who call up and the first thing say may be “we have a 28,000 square foot facility, I’d like to know what it would cost to have it swept.”
Sharon: Well tell me about that, the pricing, because I know our listeners are going to be interested. I mean is a flat fee, is it by the hour? And how much would you charge… give me some kind of example in terms of hourly or flat fees whichever one you use.
Charles: In the case like I just mentioned, where someone starts off by saying “oh, we have this large facility, we want it swept”. We’ll then say “let’s talk a little bit, let’s try to understand what is going on here, what are the circumstances”. It’s not a simple thing where you can just give a flat fee without really understanding the concerns. Typically if someone wants their whole facility swept, after we talk with them, they are happy to narrow it down to say the four or five main offices where the threat was; typically that may be the CEO’s office, the legal or financial office, conference rooms, something like that. It is because they did not understand the depth of a TSCM inspection. It may to take a long time.
One job we went to the client requested about ten offices to be swept, but when we got there he said “well, while you are here, we also have a few offices over here, a couple over there, and a few more offices on another rfloor that we would like swept as well.” The number quickly went up to twenty five offices. I had to say, “for the number of office you just mentioned we will have to be here for two or three days, so let’s narrow it down and try to get a handle on the situation.”
The cost of a sweep can vary, again, depending on the size of the space. We’re often looking at between three to five thousand dollars if it’s a local area. If we’re traveling it could be four to six to eight thousand dollars, again depending on the size of the area to sweep. It is not a five hundred dollar job. The equipment itself is very expensive. We have over two hundred thousand dollars invested in the equipment that we use. So even if someone thought they could rent the equipment to do it themselves it would cost much more than the price of the sweep.
But we try to make it affordable; we try to understand what the nature of the concerns are. When there is a very serious situation, or serious threat, then the money is not the problem. The client wants professional service and they want it done in a timely fashion. And that’s again where it’s important to understand that we do this full time. Sometimes we may get a call saying the client is having an important meeting that same night and asking if we are available, and we will try to scramble and take care of it promptly.
Usually we will have two or three technicians on an average job, and if sometimes there is a really big job we may look to bring in more people to help the job go faster.
John: Well Charles, how did you get started in this field and does it require any specific skills or education?
Charles: There is a lot of technology that we have to be aware of. My own background is that I began working in security around 1978. Now, I had some aptitude for electronics. I was a ham radio operator in my youth. You will find a lot of professionals in the TSCM field were or are ham radio operators. That’s because we have some common traits; we like to work with our hands, we like electronics, and we also have a curiosity. A curiosity to understand how things work, we want to learn about any kind of new technology.
I worked with radio as a youngster, which meant that I also understood a little about wiring, a little bit about microphones. Then when I started in the security field I helped maintain the two-way radio system, I also helped take care of telephone equipment. For instance anytime the phone company would come to service the phones on the facility I would go with them and make sure everything was handled ok. I just kept learning. Any chance I got I would try to study something related to the field.
Occasionally the company I worked for would hire someone to come in and do a sweep, for either an important meeting that was going on, or maybe a conference at a hotel. I would assist whoever was doing the sweep and I got to see a wide range of capability. Some guys really did not seem to know what they were doing. They would stay things that I knew didn’t make sense technically, again waving the “wand” around. I would shake my head and say, “something doesn’t seem right”. And then at other times there would be a countermeasures team who did know what they were doing.
So at one point I decided to go for a little training myself. After I took a class in TSCM I realized that all of my own interests, my hobbies, and all the things I had taught myself with technology came together in the TSCM field. So I decided to make a go of it.
And again, one needs a curiosity to understand how things work, a little bit of aptitude in radio, video, data, and telecom. But there is another important thing- it’s not just being a techie. You need to have a mindset for security. You’re going to be entrusted with protecting corporate assets and confidential information. So if someone doesn’t really have a good understanding of security, they are not going to do too well in this field. It’s certainly nothing like being a spy or being a James Bond character. You really have to be serious about protecting information.
Sharon: Well, give us a story or two, because I know we are running close to the end of our time. Give a story or two of interesting cases that you have handled.
Charles: Ok, there are a few I can share.
–Voicemail Hacking–
One thing we didn’t talk too much about is voicemail and phone system hacking. This is another area where now, some of the telecom concerns may be looked at from the cyber point of view, but voicemail systems have been vulnerable for many decades.
One company brought us in, well we were actually brought in by the investigation firm, the company had recently fired an employee who worked in the IT department, and he understood the telephone system. After he was fired, he called in one night, he dialed into the voicemail system and was able to navigate around the system [just by using touch-tones over the phone call].
He discovered that the CEO of the company had never changed the default password for his voicemail box. So this former employee decided to listen to the messages there and he found a message – it was an old message from an irate customer that was left there three or four months previous. The situation surrounding the message had already been taken care of, but the message was still there. It was an irate customer who spent a whole five minutes cursing at the CEO.
So the employee listened to this message and thought “here’s some fun, I can really embarrass the boss”. He knew about a voicemail feature called “broadcast message”. He was already logged into the boss’ mailbox. So he took that message and forwarded it to every employee in the entire company. That’s what the “broadcast” feature does.
So come Monday morning, all the employees come to work and every single one of them has that red light flashing on their phone. They check their voicemail, it says “oh, you have a message from the CEO”. So they all listen to it diligently and they hear this irate customer cursing at the boss with terribly foul language. So that was a little bit of harassment, a little bit of embarrassment. It took a little while but we were able to trace the details of what had happened. This type of thing you may not expect but it is something you have to think about.
–Insider Eavesdropping–
I’ve mention concern about disgruntled employees and executives even within your company. Insider threat is a big concern for all areas of security. Another case involved an executive bugging a meeting room in his own company. We found a microphone planted in a ceiling tile and wired back to the executive’s desk. This was in a stock brokerage firm. Apparently he had been eavesdropping on the meeting room where the SEC and NASDAQ people would meet to do an audit. So he was trying to listen to the officials who were auditing the company. Maybe he thought he was doing something to help his firm, but it ended up getting him fired and creating a problem for the company.
Then to add a little insult to injury, we took the microphone down from the ceiling and noticed that there was a little sticker on it from a spy shop in Manhattan. The attorney contacted the bookkeeper for the company and after doing a little search they found that the eavesdropping microphone system was purchased on the company AmEx card by this executive.
Again a little embarrassment there, but they were happy to have that resolved.

Covert microphone was found glued to ceiling tile.
–Rogue Wifi Access Point–
I can think of another time when we were sweeping executive offices and an executive dining room at technology company. We were inspecting the Wifi, checking all Wifi signals in the area. Now we know what to expect, we have been there before. We know all the access points and their labeling structure. There are other things using Wifi, too, there’s video display equipment, things like that that use Wifi. But here is one access point we detect and it is labeled “Dark Web”. We thought “is this a joke or what?”
We did some direction finding with the signal, and determined it was not in the area we were sweeping, but we found where it was coming from. We reported it to the security department who then got in touch with IT, and they were able to confirm that it was an unauthorized or rogue access point installed by an employee.
So there are a lot of little things that come up that where the purpose may not be obvious right away, we may have to dig a little bit to find out all the details behind it.
John: Charles, why don’t you tell us say, three tips that anybody can practice to help secure their information and conversations.
Charles: It’s important, first of all, to understand the value of your information and be careful of what you yourself are saying in conversations. For a company, establish good policies so that the employees know that the information they are handling is confidential.
Then from the technical perspective, some things we recommend are one, to keep an eye out for anything in your office that looks disturbed or out of place. If you left the night before and you come back and see that some furniture has been moved you may want to understand why. Was there a cleaner that came in? Was something else going on? Have ceiling tiles been moved? Moving ceiling tiles causes dust to fall down. If you see ceiling tile dust on your desk, for instance, it may warrant paying close attention to what is up above.
If you have a concern about hidden cameras, there is a small device that you can buy from a spy shop called a “Spyfinder”. It basically shine flashing LEDs toward the wall where you may suspect a camera, and then you look through a small hole in the device, if you see a reflection coming back it may from a camera lens. But you can kind of do the same thing with a flashlight. If there is a suspicious hole, whether it is in a hotel room or in an office, you can shine in there with a flashlight and if you see a reflection coming back it could mean there is a camera behind there. It may be something else, perhaps it could be an aluminum stud in the wall, but it is something that now you can investigate further. Either cover the hole, or maybe just poke a paperclip into it, see what you hit.
Sharon: I’m glad I’m not paranoid, Charles, because all this scares me. I’m going to be looking at all the holes in the hotel room walls at this point. Can you tell us how folks would get in touch with you if they had questions or wanted to engage your services?
Charles: Sure. The website is execsecurity.com. And I’m available by email at charles@execsecurity.com. On the website we have blog, it’s the News page if you go to the website. Twitter is @execTSCM and Facebook also is execTSCM.
Sharon: Well we sure want to thank you for joining us today, Charles. We’ve never had this subject discussed before and it’s a fascinating and important topic.
Charles: You are absolutely right, protection of information is critical today.
Sharon: So thank you for agreeing to join us today as our guest.
Charles: It’s been really enjoyable. Thanks very much.
