Wiretap Detection and Telecom Threats
Wiretapping is a common method for intercepting communications that has been around since wire was first used to send messages via telegraph. Confidential conversations and communications travel over wires every minute of every day. They are all susceptible to interception. Some may be more vulnerable than others. Present day communications is often run over fiber optic cables and may use digital signaling, but even those are susceptible to taps and interception.
What is a Wiretap?
The term “wiretap” is often used to refer to almost any type of intentional eavesdropping, including interception of cellular phones, radio transmitters (bugs), or other unauthorized surveillance – even though no wires may be involved. This is because the laws that govern electronic eavesdropping are often referred to as the “Wiretap Act”, which regulates the interception of any wire, oral, and electronic communications.
The “Wiretap Act” actually refers to Title III of the Omnibus Crime Control and Safe Streets Act of 1968. This act included regulating the authorized interception of communication (law enforcement) but also prohibited the unauthorized, non-consensual interception of wire, oral, or electronic communications by government or private parties.
The Wiretap Act was amended later and regulations may sometimes be referred to by other names such as the Electronic Communications Privacy Act (1986), CALEA, the Communications Assistance to Law Enforcement Act (1994), or others.
When the Wiretap Act was put in place in 1968, any electronic eavesdropping or communications interception was mainly done by real wiretaps, physically tapping into a phone line. This type of tap is still a very significant threat, even though many other forms of interception exist. Wiretapping, today, has developed into many different forms, from traditional analog taps to more sophisticated digital, VOIP, and data taps. In this discussion we are specifically referring to the act of tapping into wires or cable for interception of communications.
Traditional Analog Phone Wiring
Analog communications are the easiest to intercept. It can be done with simple tools and techniques, in some cases just clipping on to a wire with a speaker may be enough to allow eavesdropping on conversations.
Even though analog phone systems are less popular today (many have been replaced by more modern digital equipment) they are still used extensively in many forms and must be inspected carefully along with the more sophisticated digital systems. Digital phones systems may also use analog wiring for the both phone company connection and for certain extensions. Many popular conference phones will use an analog extension as part of a digital phone system. That means the wiring from the conference phone all the way back to the PBX room will be analog and very easily tapped.
Analog phone lines remain one of the most common forms of connection to the public telephone company network. POTS lines, as they are often called- for Plain Old Telephone Service, may still be in use as the main outside lines for a company, but even if a business has transitioned to digital lines (“SIP” trunks and VOIP service), analog lines will often still be present as a backup service, for use in the event of an internet failure or power failure.
Though your phone communications may travel to your facility in a digital form – such as from fiber optic cables, over Cable TV wiring, or from other internet VOIP service – they still may be converted to analog before they connect to your phone equipment. The digital service brings the connection to your office or home, but there will typically be a converter box that changes the signal back to an analog connection to be able to interface with standard telephone equipment.
The wiring within your facility offers many opportunities for wiretaps to take place. Skill and care is needed to be able to trace wiring properly. Our technicians have experience working with a number of PBX models and in a variety of cabling situations. We have a number of tools that allow tracking and tracing of suspicious wires or taps.

Analog phones may be desk phones, wall phones, or other designs and are often used as back up phones in case of power failure.

Popular conference phones are often analog models that are easily wiretapped.
PBX Telephone System Wiring
Analog PBX systems
Analog phones systems still exist in many offices and homes. They may even be twenty or thirty years old, yet work fine, so the users find no need to replace them. In these systems, every extension as well as the phone company lines are vulnerable to easy interception using simple listening devices or recorders.
Digital telephones and Hybrid PBX systems
Digital PBX system came on the scene in the 1990s. They became very popular and added a level of difficulty when it came to wiretapping. The digital signal from the phone extension could not be listened to by simple amplifiers or recording devices. Within a few years of their introduction though, inexpensive “demodulators” were introduced that could convert the digital signal so it could be recorded easily.
A number of digital PBX systems are referred to as “hybrid” systems because they allow the use of both digital and analog devices. Many popular conference phones will use an analog extension as part of a digital phone system. That means the wiring from the conference phone all the way back to the PBX room will be analog and very easily tapped.

Analog and hybrid PBX systems are still very much in use in offices as wells as executive homes. Often using analog outside lines.

Companies with VOIP systems still may use analog lines for power-fail and for conference phones.
System Call Monitoring
“Your call may be monitored for quality assurance…”
All major PBX systems come with a feature, that many are not aware of, called “supervisor monitoring” or “silent observation”. This feature is intended to allow a supervisor to listen in to conversations between an operator and an outside call. This feature is easily exploited for eavesdropping. Sometimes this might be referred to as a “software wiretap”. Finding and securing a software tap or other PBX programming vulnerability is an important area that we can assist with.
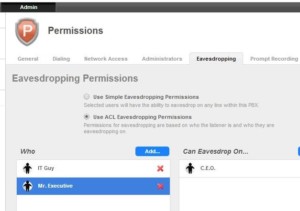
VOIP systems also include call monitoring (aka eavesdropping) as a feature.
VOIP and Network Communications
Wiretaps also exist for VOIP and data. Taps can be inserted in the line with phones and computers to allow siphoning off data. Recorded data signals can be reconstructed to reproduce the audio from VOIP phone conversations.
Inspection of data closets and patch panels should be performed if there is an suspicion of this type of wiretap taking place.
As mentioned in traditional PBX’s above, supervisor monitoring is also a feature in VOIP systems. The wide area capability of VOIP, to have users and administrators spread over many different locations, could allow someone to intercept conversations from a totally different city.

Wiretaps for LAN connections can be placed in between network cables to route data to a remote location.
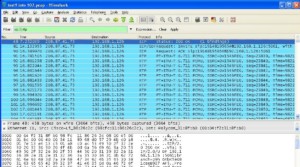
A LAN wiretap allows interception of data packets that can be recorded via software.
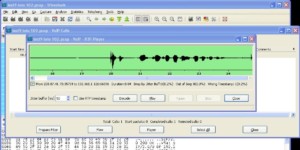
Software can translate VOIP data back into voice for eavesdropping purposes.
Paging and Intercom Systems
It is important to recognize that any device with a speaker in it can also act as a microphone. Thus speakers that may be used for paging, intercoms, or even background music could be intercepted and used for eavesdropping on the room where they were located.
Intercom and paging systems make use of wiring that runs throughout your building. It could be possible to tap into the wiring in a one part of the building to listen in to conversations taking place in a totally different area.
A typical vulnerability we find is that paging speakers mounted in the ceiling can act as microphones simply by attaching an amplifier to the wire, allowing someone to listen to conversations from every room that has one of the speakers in it.
Many buildings have old systems that may have been abandoned in ceilings with the wiring still in place. Tapping this wiring can provide an easy method for eavesdropping to occur.

Ceiling and paging speakers can be used as microphones.

Wiring for ceiling speakers is exposed in ceiling and in wiring closets.

Wires in the ceiling may be a mess and require special tools to trace.
Telecom and Data Equipment Modification
Desk phone modification
Desk phones need to be inspected to be sure that no modifications have been made to the internal circuitry or wiring. Simple modifications could allow the microphone of the telephone to send room audio over the wiring where it could be picked up elsewhere in the building. Small transmitters or recording devices could also be hidden within the phone circuitry or housing.
Spare pair wire interception, microphone connection
Telephones and data wiring often have extra wire conductors. The spare wiring could be used for connection to an internal microphone or speaker. This could allow an eavesdropper to intercept communications by wiretapping those conductors from another location. This could be a wiring closet, from the IT or PBX room, or the wires could be spliced to another location in the building. Any suspicious wiring will need to be traced to determine it’s destination.


Telephone unit inspected for modifications or taps.
A miniature microphone can be installed in a data cable plug to be tapped off at a wiring closet or patch panel.
Tools for Wiretap Detection
Typical tools and tests used for analyzing cables and detecting wiretaps include:
- Audio analysis, testing wires for any indication of room audio.
- Electrical and electronic properties, voltage, capacitance, and other characteristics.
- TDR and FDR equipment- Time Domain and Frequency Domain Reflectometry which will display graphic analysis of wires under test to reveal any wiretaps, splices, or other anomalies.
- RF tracing tools that inject a radio signal onto the wires so they can then be traced at extended distances.
- Ethernet testing for pair analysis and proper network configuration.
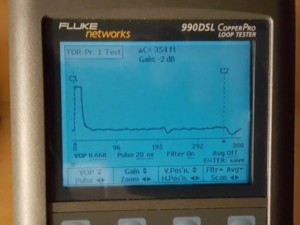


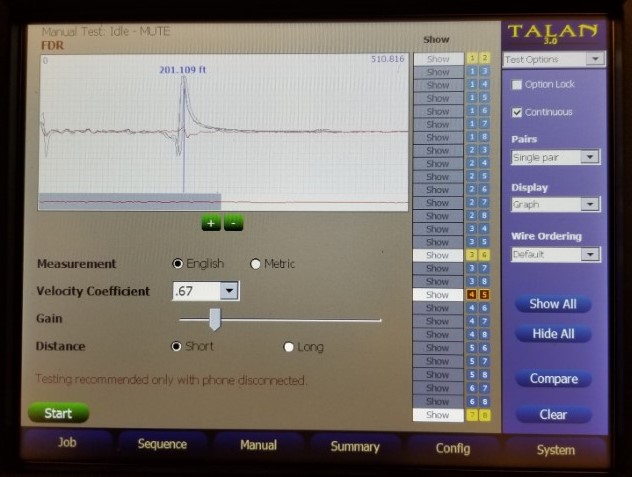
Time Domain Reflectometer (TDR) allows identification and location of wiretaps, splices, and other anomalies.
Wires can be inspected for the presence of audio to determine if they may used for wiretaps or other eavesdropping.
Testing of wires for voltage and audio on a telecom punch block.
Analysis of wiring and telecom data communications can be performed using advanced test equipment.
Tracing Wiring in Telecom Rooms
We have extensive experience working in many wiring environments. To detect and locate wiretaps, it is necessary to be able to differentiate which wiring is proper and important and which might be suspicious.
Telecom rooms are often filled with unused wires that could be used for unauthorized taps, and also wires that may look old and abandoned yet still be in use.

TDR testing telecom wires.




Your telecom room may look like one of these. We have experience in all types of wiring environments and will work with your IT or telecom department when necessary. We know which circuits are critical, and which may be vulnerable. We can be trusted inspecting your cabling.
