TSCM Sweeps for Hotel Meetings, Board Rooms, Conference Centers
Confidential Meetings Require Security
Business meetings and conferences often discuss sensitive and confidential matters that may require significant security preparations. Depending on the level of discussions taking place, there could be serious risks including exposure of trade secrets, damage to company reputation, or high financial loss at stake. It is the fiduciary responsibility of the corporation to the shareholders to insure that significant security measures are in place.
Loss or leak of even a small amount of confidential information could have serious and damaging affect on a company or on the individuals within that company. This could include affecting stock prices, loss of information to competitors, and leak of scheduling information resulting in physical danger to executives.
Some examples of meetings involving sensitive information include:
- Board meetings
- Planning meetings of interest to competitors
- Discussion of upcoming activities involving personnel with high threat potential
- New product information or release dates
- Design details
- Research and development activities
- Company mergers or acquisitions
- Discussion of legal issues including ongoing litigation
- Stock offerings or announcements
- Contract negotiations
- Personnel changes, including firing of executives, CEO, or President
Loss of any such information could have a devastating effect.
Competitors, political opponents, legal adversaries, and anyone desiring to do harm to your company could pose a threat. Often this threat comes from persons already within your organization who think they will boost their own status by releasing any information they can get hold of.


Electronic Security Bug Sweeps
Electronic security bug sweeps of meeting rooms are necessary to help prevent eavesdropping and corporate espionage activities from taking place.
What are possible threats?
Things we would be looking for include hidden microphones or transmitters, covert cameras, and any vulnerability that could result in information leaks. We perform a number of detailed electronic tests as well as a thorough physical inspection of the area.
Vulnerabilities
Vulnerabilities are often found that would not normally be considered an attempt at spying. This could include air vents or passages that allow sound to pass to a different room. That second room may need additional security. Audio and video systems might have wireless devices, such as assistive listening systems, that could transmit conversations well beyond the boundaries of the room. We can locate such equipment and make appropriate recommendations.


Hotel Audio/Video Systems Are Not Secure
Hotels may have their rooms pre-wired with microphones, jacks, and speakers. This allows for easy set up and flexibility for their guests. But if a client is having a confidential meeting, the hotel system could allow compromise of the audio by house technicians or others. The hotel audio wiring may be interconnected through many rooms and the sound could be easily intercepted or diverted. When that is a concern, we recommend bringing in a separate sound system not connected to the hotel wiring.
Wireless Microphones
Many presenters are desire to use wireless microphones for convenience. When privacy is a concern, we always recommend our clients to make sure that either no wireless microphones are used or if they are truly needed, they should be digitally encrypted systems. Older analog wireless microphones are very easy to intercept and do not provide adequate security. The cost of digitally encrypted microphones has come down considerably in recent years, so most AV companies should be able to provide them. We can make recommendations if needed. If the hotel offers to supply a wireless microphone, it may very likely be an older analog microphone which should not be used.


Examples of Problems
Hotel technicians may have ability to eavesdrop on any room at any time. At one facility we visited, the hotel AV technician was proud to explain that he was able to listen-in to any meeting room in the hotel from his control booth. He clearly did not have privacy of the clients in mind.
At another location, the client made it clear that no wireless microphones and no recording were to be present in the room. Even so, we found an analog wireless microphone belonging to the hotel that had been left in a drawer in the back of the room. The mic had fresh batteries and was ready to begin transmitting. It needed to be removed or disabled and secured prior to the meeting.
We swept a large auditorium that had many microphones permanently installed throughout the room. The sound system was always under control of the AV manager, but even so, we discovered that there was a defective piece of equipment in the audio system that was transmitting an analog radio signal of all sound from the room. The signal was strong enough to be received from the parking lot of the building with a simple radio scanner. We were able to identify and remove the defective device prior to their meeting.

Even though the client requested that no microphones be allowed in the room, a wireless mic was found powered on in a drawer.
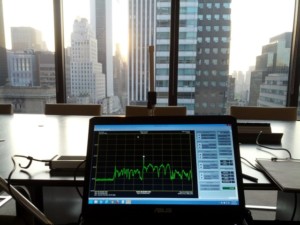
Real-time Signal Analysis and Monitoring for Meetings
In situations where there is a need to be sure no cellular, wifi, or other devices are transmitting during the meeting, we offer real-time analysis of the radio spectrum in a conference room. Antennas connected to our equipment can be set up prior to the meeting while our radio receivers and spectrum analyzer are deployed in a nearby room to monitor all signals. If any suspicious transmissions appear we would have a procedure in place to inform the host so that steps could be taken to prevent information loss.
Learn more about Real-time Signal Analysis on our page here.
Additional Security Measures
Some clients need to take extra steps to ensure that no recording devices or transmitting devices – including cell phones – are brought into the venue. Security measures could include using X-ray machines and metal detectors for attendees and their personal items. Walk-through cell phone detectors are also available as well as portable “faraday” boxes which block radio signals, where organizers will collect participants’ cell phones to insure that no phones are transmitting from the area.
The level of security needed will depend on the risk involved. High value targets could require multiple countermeasures to be undertaken.
Please contact us regarding your upcoming meetings. We will be happy to discuss your concerns and the find best way to provide security for your meetings and confidential discussions.

Plan for Meetings Properly
Be sure that information security is included in the organizing of all important conferences. Privacy may not be a priority in the minds of those planning the meetings. We are always ready to assist with preparations for any special events you may have.