Security check vs reality check
It’s time to double check your security procedures when your CEO stumbles upon a spy sitting in your conference room.

This is what happened at Raynham, MA robotics firm Medrobotics. CEO Samuel Straface was leaving the office the evening of August 28 when he spotted a man he did not recognize working on a few laptops in a company conference room. After being confronted the uninvited guest explained he was there to meet a couple of executives of the company. Straface knew that one was out of the country and the other did not have such meetings scheduled. The intruder then claimed he was there to meet the CEO, Samuel Straface, himself.
At this point Mr. Straface knew the man was up to no good and called the police.
The man said his name was Dong Liu and claimed that he was doing patent work for a Chinese law firm. The police arrested Liu and referred his case to the FBI.
Liu’s LinkedIn profile says he is a senior partner at Boss & Young Patent and Trademark Law Office of Greater China- leading the firm’s Intellectual Property (IP) practice in medical device, bio-tech, clean-tech, and other emerging high-tech areas such as new media. He was also responsible for the firm’s IP licensing and transaction services.
According to American Lawyer (international.law.com)
On Boss & Young Beijing’s website, Liu was listed as a senior partner who led the firm’s “intellectual property practice in medical device, bio-tech, clean-tech and other emerging high-tech areas such as new media.” The firm has since removed Liu’s profile from its homepage, but the website remained searchable.
When contacted via phone by The Asian Lawyer, ALM Media’s Asia publication, an employee at Boss & Young Beijing said “our company doesn’t have anybody named Liu Dong.”
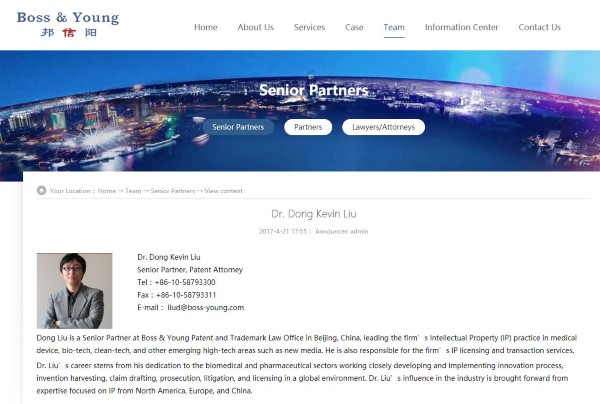 Profile of Dong Kevin Liu, found on Boss & Young’s website.
Profile of Dong Kevin Liu, found on Boss & Young’s website.
When he was arrested, his car was also searched.
According to CSOOnline.com he was found to have the following items in his possession:
- One white Apple iPhone with a gold Mophie case
- One 16GB smartwatch
- One 128 GB thumbdrive
- Two digital camcorders
- Seven SIM cards, one SD card, and one thumb drive
- One Apple watch, serial # FMLQ9803GR7M
- One white Hisense smartphone
- Two Seagate portable drives – 2TB
- One Apple MacBook Pro Model A1502
- Three SIM cards and two Micro SD cards in a clear plastic case
- One Microsoft Surface 128GB computer, serial # 014881654353
- One Apple iPad, serial # DLXT702UGMW7
An article at Stratfor.com, a global intelligence firm, points out that Liu may have been planning serious espionage:
… Liu spent 2.5 hours inside the company’s headquarters and had two video cameras. These facts probably indicate that he intended to do more than attempt to breach the company’s computer systems. Indeed, one doesn’t necessarily have to be inside an office building to hack into a company’s wireless network. Rather, it appears that Liu was waiting for the staff to leave so he could roam through offices, labs and cubicles and record anything he could find of potential value.
In addition to carefully examining Medrobotics computer networks to determine whether Liu was able to gain access or plant malware, the company will likely conduct a technical security countermeasures sweep to ensure that Liu did not plant any bugs.
A reason for TSCM
This is one of the reasons for conducting regular proactive TSCM sweeps. If there has been an intrusion at your facility, you need to be able to detect and eliminate any electronic surveillance that may have been planted. And, if any device is found, it is important to know how long it may have been in place. This will help identify what information, meetings, or conversations may have been compromised.
Lucky for Medrobotics that their CEO was alert enough to spot and identify the intruder. How easy would it be in most facilities for such incidents to occur yet go unnoticed?
Penalties for theft of trade secrets
A statement from the US Attorney’s Office of Massachusetts indicates that the charge of attempted theft of trade secrets provides for a sentence of no greater than 10 years in prison, three years of supervised release, and a fine of $250,000, or twice the financial gain or loss, restitution, and forfeiture. The charge of attempted access to a computer to obtain information unlawfully provides for a sentence of no greater than five years in prison, three years of supervised release, and a fine of $250,000.
Security awareness needed
All aspects of security are necessary to protect against corporate espionage. Physical security, access control, cyber security, and TSCM electronic sweeps are all be critical elements needed to secure your information and confidential communications. Perhaps more importantly, a keen awareness of potential security problems and a readiness to act may prevent severe loss of intellectual property.
More on this case can be read at:
Stratfor.com
International.law.com
US Dept of Justice
CSOOnline.com
