If you thought Morse code was only from a past, bygone era, you may want to think again.
Ages ago, when I was struggling to get up to 13 words per minute for my general class ham radio Morse code exam, there was some value in knowing Morse – Boy Scouts, ham radio, pilots, navy, and for sending messages when you are held captive- see “Rear Admiral Jeremiah Andrew Denton” who, as a POW in Vietnam, was able to let the US Intelligence know of his condition by blinking the word “TORTURE” in Morse code with his eye lids.
The straight carrier signal used for sending the code over radio waves allowed the information to travel with more power than voice, and it would cut through the noise encountered when trying to receive the message. Morse messages were likely the first text messages sent over radio waves (over wire, too, for that matter).
As personal computers emerged on the scene, a number of software based Morse encoders and decoders were developed, so the necessity of learning to hit the code key cleanly or to interpret the code in your head diminished.
The code itself, though, lives on and continues to be used in a number of ways, but finding it used for a cyber attack is pretty unique.
Bleeping Computer reported on a phishing attack that utilized Morse code to hide malicious URLs from being detected by secure mail gateways and mail filters [here].
The attack was sent in an email alleging to be an invoice for the target company. It included an attachment that at first glance appeared to be an Excel spreadsheet, but was in reality HTML code, such as “[your_company]_invoice_123456.xlsx.hTML.”
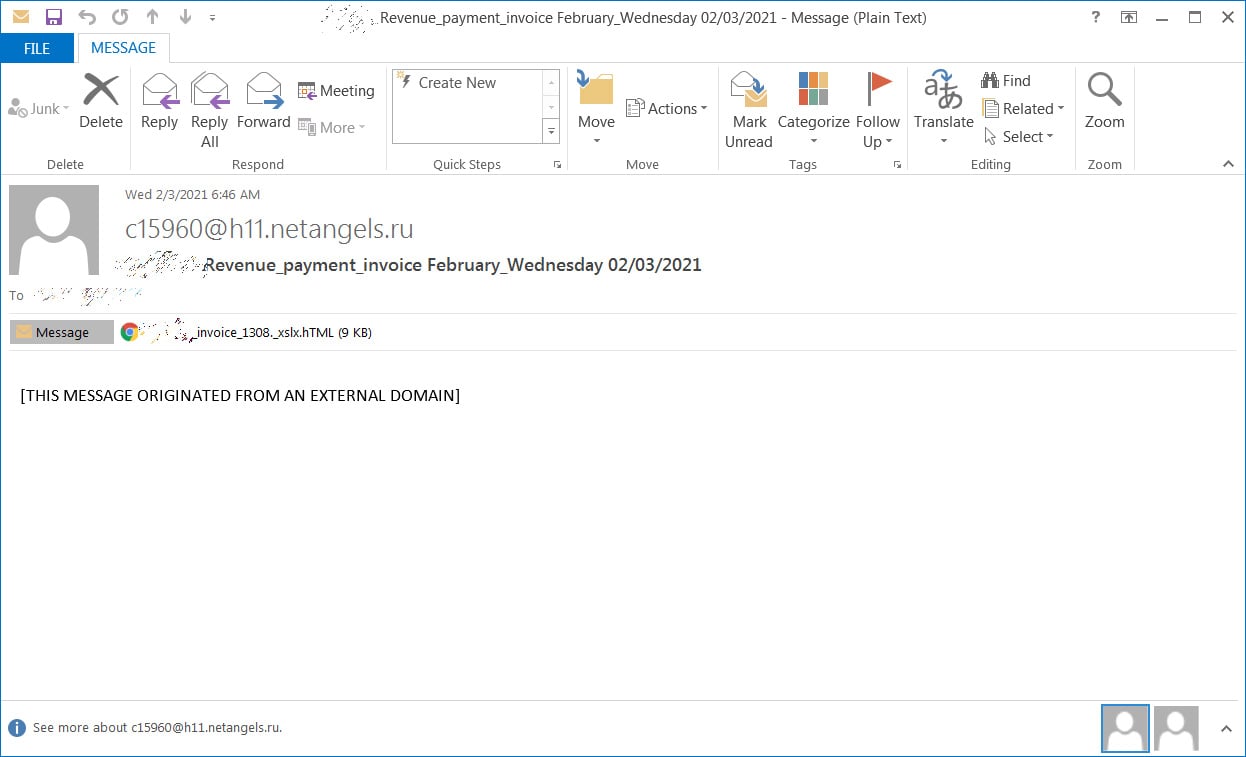
The HTML code included a Morse code decoder that could map the dots and dashes (“dits and dahs” for you ham operators out there) into the appropriate English letters and numbers.
That code would create a fake Excel spreadsheet with a fake pop-up saying that the user needed to re-enter their password to continue. Of course, the password entered would be forwarded to the attacker.
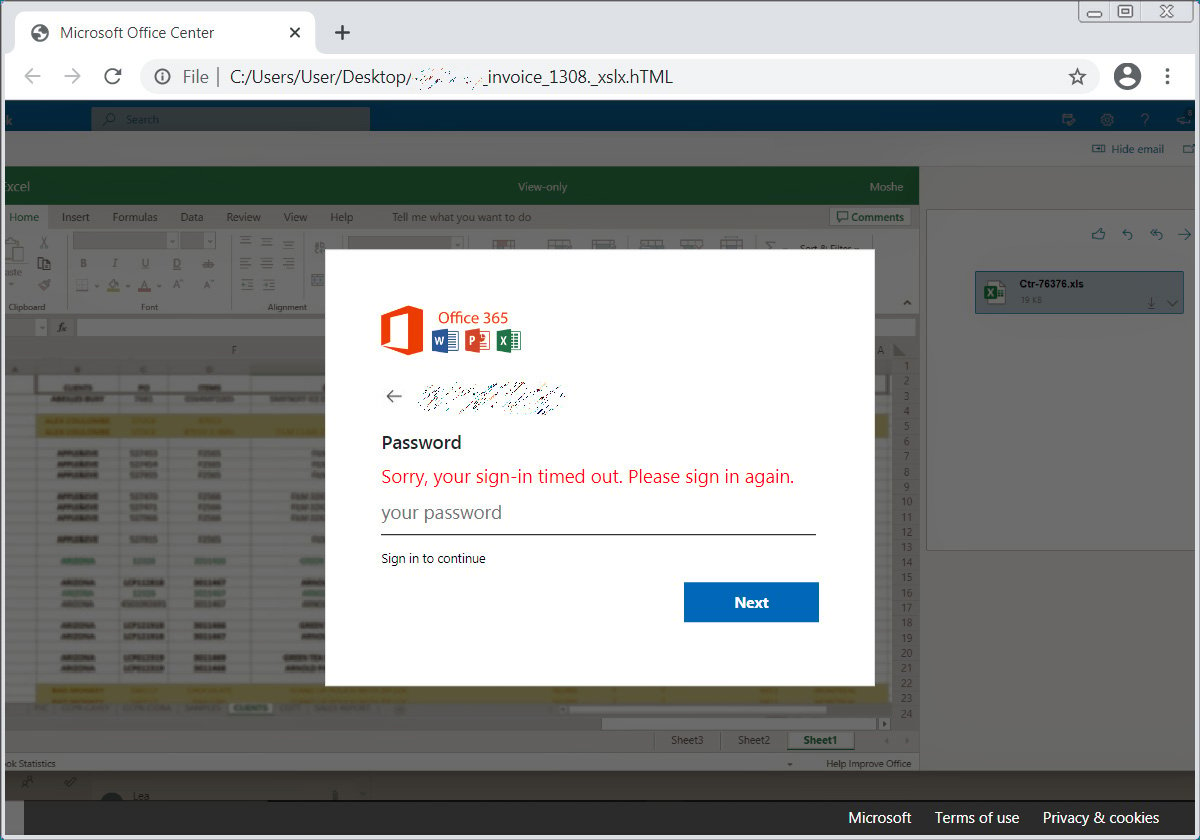
Recommendation: you MUST pay close attention to the URLs and attachment names of any links or requests for information, and do not submit any sites or forms that look even remotely suspicious!
Read more at Bleeping Computer.
