
Recently revealed at the 2021 RSA security conference and reported in TechTarget, researchers from cybersecurity firm Guardicore were able to successfully turn Comcast voice remotes into eavesdropping tools, covertly recording conversations via the remote’s microphone.
 Guardicore Labs senior researcher JJ Lehmann and vice president of research Ofri Ziv explained how an attacker in close proximity to the target could trick the XR11 into downloading a modified version of the firmware that added a command to record and transmit audio via the on-board microphone the remote uses for voice commands.
Guardicore Labs senior researcher JJ Lehmann and vice president of research Ofri Ziv explained how an attacker in close proximity to the target could trick the XR11 into downloading a modified version of the firmware that added a command to record and transmit audio via the on-board microphone the remote uses for voice commands.
Hang on, don’t throw out your remote yet, it’s not that straightforward.
The update is not something that can be done over long distances, and required much effort and preparation.
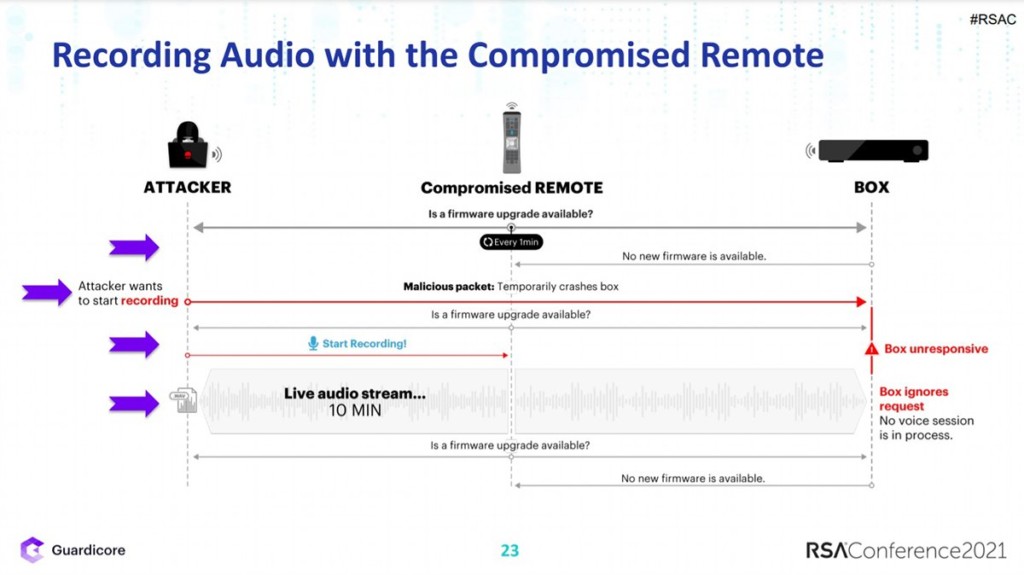
Guardicore discovered a new attack vector on Comcast’s XR11 voice remote that would have allowed attackers to turn it into a listening device – potentially invading your privacy in your living room. Prior to its remediation by Comcast, the attack, dubbed WarezTheRemote, was a very real security threat: with more than 18 million units deployed across homes in the USA, the XR11 is one of the most widespread remote controls in existence.
A bad actor, though, would have to be within short physical range of the remote control (Guardicore’s demo worked up to 64 feet) for upward of several hours in order to send the RF signals that would be needed to manipulate the firmware and set up the attack. This is not the sort of thing that can be pulled off from a remote location, you would need to be literally near the remote’s location.
Guardicore notified Comcast of the vulnerability last year and they were able to patch their systems in September. Guardicore released a blog post about it in October which can be read [here].
How the attack works.
More information can be found at:
Guardicore and
TechTarget.com
