Details have emerged of a recent eavesdropping and bugging operation at a West Palm Beach law firm that reveal classic eavesdropping techniques. Looking at the details, we find some things they did right, and some things they could have handled better. Or put another way – “why you should have a qualified TSCM sweep team on your side”.
The law firm of Steinger, Iscoe & Greene (SIG) is suing Michael Coronel, a paralegal and private investigator, for allegedly placing recording devices within the ceilings of its West Palm Beach office without permission.
The private investigator worked exclusively for an attorney at SIG, Lee Levenson. Levenson was later fired from the firm. Authorized surveillance cameras in the facility caught Michael Coronel entering the building after hours with an accomplice to install the eavesdropping devices.
The activities were reported in the West Palm Beach Post:

Microphone discovered in ceiling tile
When the firm’s finance director found drywall debris on the floor of her office when she came to work on Sept. 10, she asked a maintenance man to pop up a ceiling tile, according to West Palm Beach police who were summoned to investigate two days later. There, hidden in the recesses of the ceiling, the finance director and others discovered wires that were linked to an audio receiver, police said.
As part of the investigation, police said they found wires running to cameras, microphones and recording equipment mainly in the firm’s finance, marketing and human resources departments.
Some of the wires had been cut and a video recording device was missing. Pike said it appears whoever installed the devices hurriedly removed the digital recorder once they realized police had been called.
The full document can be found [here]:
Highlights worth noting.
Review of the court filings reveal a number of aspects of the case that can provide helpful insight into ways to better protect your offices and your confidential information, and ways to be better prepared in the event an eavesdropping incident does occur.
Finance director paid attention.
The firm’s finance director noticed some debris on the floor of her office. She was wise to see this as potential problem and notified the company that someone may have entered her locked office after hours.

Maintenance department discovers device.
The maintenance department was contacted in case there had been work done in the office, they said that no work had been done there. They proceeded to open the ceiling tiles and spotted the devices there.
Police and OCU called, more devices found.
Police were contacted, and in turn, called the Organized Crime Unit. Additional devices were found in the HR Director’s office and the Marketing Director’s office.

IT Department continues search, additional device found.
After this, the company asked their IT department to conduct a search of every office. One more device with video capability was found in a paralegal’s office.

Valuable lessons
There are a number of valuable lessons that can be learned from this series of events.
Awareness

Physical inspection of areas is always a good thing.
First, kudos are due the finance director for noticing the debris in her office and not passing it over. Anything out of place could be an indication that nefarious activities may have taken place. As the saying goes- “if you see something, say something”. That applies in information security, too. Furniture moved, debris from ceiling tiles, doors found unlocked, they may have a legitimate reason, but if you are concerned about privacy and confidentiality, then there is no harm in finding out what happened.
Second good thing, the building maintenance department did not pass it off as just some kind of fluke or accident. Not only did they make the effort to look in the ceiling, they were able to recognize that things were not right there. At this point, though, the company should have contacted a professional countermeasures firm to assist and at least provide some guidance. Apparently, between the time the devices were spotted and when the police responded, someone was able to remove some of the eavesdropping equipment.
Police response
There is a plus and minus given for the police contact and response. Local police rarely deal with eavesdropping concerns and may not recognize the significance to the company or may not even want to get involved. I have had occasion to reach out to the FBI regarding certain cases and they explained that they were willing to get involved only when there has been a serious breach and the victim intends to pursue the case and press charges. Many corporations, though, would rather resolve such problems quietly, in house.
In this case the police realized it was an area they were not experienced with and reached out to the Organized Crime Unit. This situation, though, did not really have much to do with organized crime either, so they may not have been enthusiastic about getting involved. It seems that they were able to assist, though. The OCU typically would have personnel experienced in placing and installing listening devices, but perhaps not so familiar with the extensive tests and techniques needed for searching for the multitude of possible devices.
IT department
Next, SIG asked their IT department to follow up and continue searching throughout the facility. This could be considered a bold error. This is the point where they really needed to contact a professional TSCM provider to conduct a full sweep of the facility. The IT department could certainly be of assistance, but they would not be experienced in specific eavesdropping countermeasures techniques. Sometimes people may think “Oh, it’s technical? Then let IT take care of it, they understand technology.” In many eavesdropping cases, there may also be a concern that someone in the IT department was involved. That is another good reason for having an outside third party to assist.
As soon as one type of device was found, it should also have been recognized that there may be many other types of devices present. Not just wired microphones or cameras, but perhaps radio transmitters, wifi or cellular devices, or other sophisticated devices that would not be found just by simple observation.
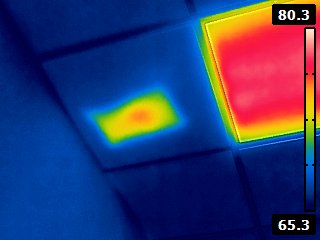

Thermal Imaging is one specialized test that helps to discover hidden devices.
Multiple devices, multiple areas
A very important aspect of this case is to recognize that finding one device or a breach in one office does not mean the work is done. Here devices were found in at least 4 different areas- accounting, human resources, marketing, and a paralegal office.
CCTV
One more good point is that the facility had working CCTV cameras that were able to identify the perpetrators. After a crime has been committed, it is often found that the CCTV on premise was either poor quality, in need of maintenance, useless views, or even just had the wrong time setting for example. Ensuring your facility has a good quality, working camera system is very important to following up on possible crimes.
Breach of confidentiality
The law firm now needs to recognize that it has now suffered a serious breach of confidentiality that could impact ALL of their clients. A thorough TSCM inspection of their facility is necessary to be able to ensure privacy and confidentiality for all of their cases and clients.
Connect with a reputable countermeasures firm
It is wise for all large firms to have a good working relationship with a professional TSCM sweep provider for just such a situation. All high profile law firms, accounting firms, health care providers, and so many others should consider having proactive electronic sweeps done periodically at least as due diligence. The need may be more serious if there are significant cases and litigation in progress. If SIG had done this they may have discovered much more going on, discovered it sooner, or even better, they may have prevented it from occurring in the first place.
Confidentiality
Even though electronic sweeps are done discretely, the awareness that inspections are done periodically does not need to be kept secret. Employees AND executives need to know that their conversations are meant to be private and confidential, and that any form of eavesdropping or unauthorized recording is forbidden. It should be clearly detailed in company policy. That knowledge alone may cause insiders to think twice before attempting such activities. Regular TSCM sweeps could have prevented the breach and associated trouble at Steinger, Iscoe, & Greene.

