Need secure conversations? Try the new Privacy Suite in the Rolls Royce Phantom.
Rolls Royce has introduced their new "Privacy Suite" for the Phantom extended wheelbase model. No more listening in (from the front seat) to the conversations of the CEO or celebrity, in the rear. The Privacy Suite uses electrochromatic glass (also known as "smart glass") to separate the front seats from the rear compartments. They have also added a "frequency specific" sound-absorption material that inhibits the transmission of conversations from the rear to the front of the vehicle.







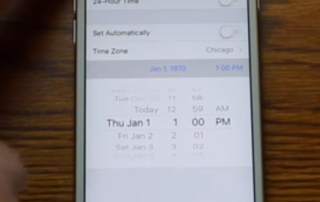
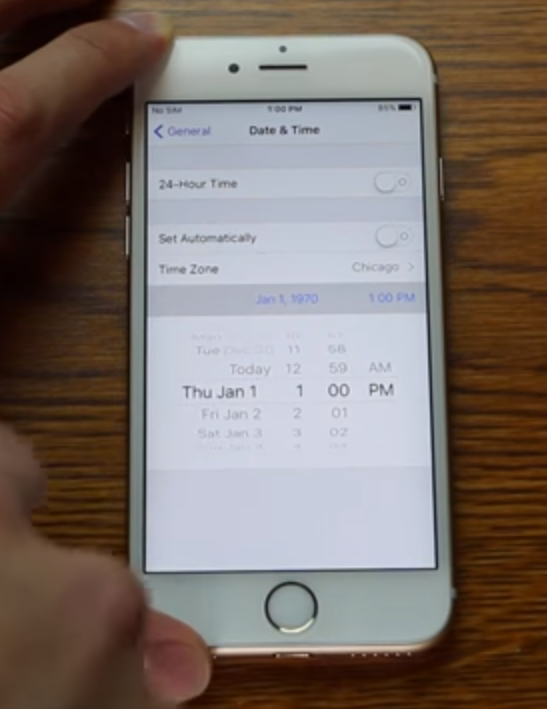 Zach Straley demonstrating the fatal Jan. 1, 1970 bug. Don’t try this at home!
Zach Straley demonstrating the fatal Jan. 1, 1970 bug. Don’t try this at home!  Advanced parts made by 3D printing could be at risk.
Advanced parts made by 3D printing could be at risk.  The Palace of Westminster Photo: Geoff Pugh for the Telegraph
The Palace of Westminster Photo: Geoff Pugh for the Telegraph 
 Three employees at Wyman-Gordon in Grafton, Massachusetts, facing felony wiretapping charges for setting up a hidden camera with audio to record their coworker.
Three employees at Wyman-Gordon in Grafton, Massachusetts, facing felony wiretapping charges for setting up a hidden camera with audio to record their coworker.