TSCM Tools and Techniques
Technical Surveillance Countermeasures, or TSCM, refers to methods of protection against technical or electronic surveillance. A number of countermeasures tools and techniques are used in our sweeps.
At Exec Security we regularly research new threats and new technology to insure that we have the ability to protect against all eavesdropping and technical surveillance threats.
Call us now if you suspect any problems with privacy, corporate espionage, or surveillance devices. We are always happy to discuss your concerns and make recommendations at no cost.
Radio Frequency Analysis
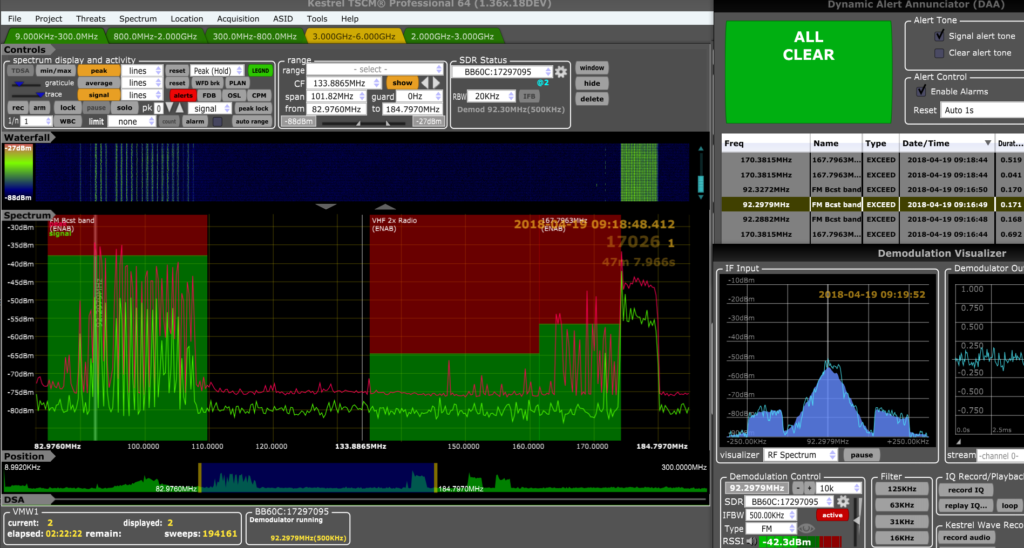
Many eavesdropping devices use radio signals to send audio or video out of the target area. One of our main TSCM tools is the RF spectrum analyzer. This instrument provides a visual display of all radio signals found in the vicinity. Through this device we can see not only the strength of the signal but also the exact frequency, steps can then be taken to locate the source of the signal. Many of our spectrum analyzers are computer controlled, allowing trace comparison of multiple signals and locations, automated alerts, and other complex analysis of signals.
Other specialized receivers are used in TSCM that are dedicated for certain tasks. These include detecting cellular and GSM transmitting devices, checking for “near field” signals to narrow down and pinpoint the location of a transmitter, and checking power lines and other wiring for low frequency or “carrier current” signals.




Electronic Device Detection
The Non-Linear Junction Detector, or NLJD, is a highly specialized tool that can detect electronic devices, even if they are not turned on or active. NLJD can find electronic components that may be disguised or hidden in other objects such as books, furniture, or woodwork. Sometimes referred to as a “broom”, the NLJD is one of the most important TSCM tools.


Thermal Imaging
Electronic devices will generate heat when they are powered on. We use Thermal Imaging in a TSCM sweep to determine if there are any signs of heat in places where it should not belong. Thermal readings from cameras and eavesdropping devices may show up in ceilings, behind walls, or in many other locations. Any such readings will be investigated to determine if the source may be a surveillance device.


Thermal image reveals electronics hidden inside an air vent.
Telephones & Wiring
Telephone devices and wiring have always been a target for eavesdroppers and corporate spies and are an important aspect of TSCM sweeps. We inspect telecom equipment and associated wiring for any abnormalities that could indicate tampering or other eavesdropping vulnerability.
Telephone lines that connect to the outside can also be inspected. They might be from the local phone company, cable company, or digital lines, each mode has its own strengths and weaknesses that should be evaluated.
We have experience and training with many varieties of PBX telephone systems which also may have unique vulnerabilities. We can look at your system and identify threats and vulnerabilities that may exist there.
Voicemail hacking is another area plaguing many businesses today that should be considered in TSCM. We have helped solve a number of hacking incidents where PBX’s and voicemail systems had been compromised causing unauthorized toll charges, theft of information, and corporate harassment.
For problems ranging from simple wiretaps to sophisticated hacking, we can be trusted with inspection of your telecom system.
Read more about wiretap threats and detection on our wiretap page.

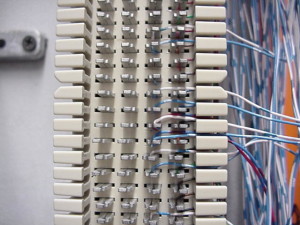


Wiretap found on a punch block in a corporate telecom room during TSCM inspection.
Does your wiring look more like this? We have the tools and experience needed to trace these lines.

Testing of VOIP phones uses specialized data equipment.
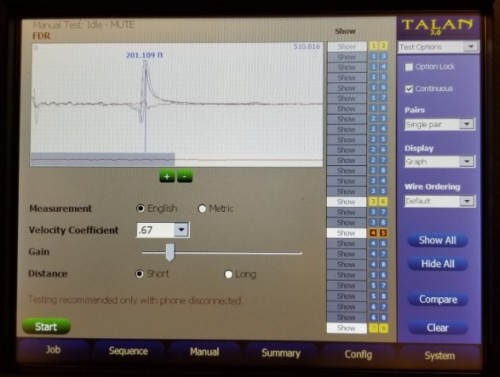
Advanced wire testing can reveal taps and devices planted on cables.
Networks, Wifi, & Cyber Security
An important security concern is your computer network. There are many areas that firewalls and other typical cyber security measures cannot protect. Many vulnerabilities exist in areas where the data network connects with wiring and hardware devices. TSCM sweeps are necessary to secure the gap that exists between cyber security and physical security.
Network ports, wiring, and data jacks can be easily compromised. We test cables and jacks to insure proper interconnections. Small microphones have been found embedded inside data cable plugs.
Unsecured wifi and rogue access points can allow a cyber intruder to gain access to the corporate network. Many stand alone eavesdropping devices are also able to use wifi to send their audio or video out of the target area beyond the range of typical radio transmitters. We inspect all wifi signals in the area to detect such vulnerabilities.
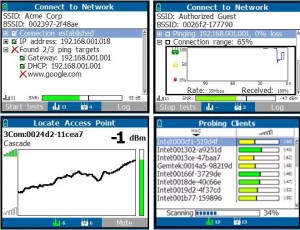
Physical Inspection
One of the most important parts of a TSCM sweep is the physical inspection. We inspect all areas in and around the target location. This will involve inspecting furniture, ceilings and soffits, electric outlets, cabinets, and any location that could conceal surveillance devices.
Along with standard tools and flashlights, we also use micro video cameras that help to view inside small holes, crevices, and compartments that may be difficult to inspect visually. Many devices and vulnerabilities are found during the physical phase of the TSCM sweep.


