Real-Time Signal Analysis
for protection of confidential meetings.
also known as In-Place Monitoring, or “Live” Monitoring
Protection during confidential meetings
Boardrooms, conference rooms, and other meeting areas often require technical protection to ensure that no eavesdropping or espionage activities are taking place during important meetings. Such threats often come from radio transmitters (bugging devices) that may have been hidden within the room intercepting the conversations and discussions taking place.
An electronic TSCM sweep (Technical Surveillance Countermeasures) should be performed of the area prior to the meeting, but that may not eliminate all threats. Listening devices may be brought into the area after the sweep was completed such as by staff or workers who are preparing for the meeting; or by participants – either knowingly or unknowingly; or there might be remote activated transmitters that only reveal their signal during the meeting. Another potential concern may be from unanticipated or even defective audio equipment that is activated at the time of the meeting, such as wireless microphones or other equipment that may unknowingly be transmitting audio out of the area.
Because of these concerns, there is a need to protect the room during the active meeting. Real-time monitoring, also referred to as live monitoring or in-place monitoring, involves analyzing the radio signal environment in the vicinity of confidential meetings in real-time in order to detect the presence of any illicit or unauthorized transmissions in the area.
Real-time monitoring is confidential
It is important to recognize that in this usage, the term “monitoring” does not refer to listening to any conversations from the room. The TSCM technicians are only observing the radio signal spectrum and are not listening to or recording any confidential activities in the room.
Tests and equipment
There are a variety of tests and types of equipment that are used for real-time monitoring. We will describe some of them here.
Radio Frequency (RF) Spectrum Analysis is the most common and effective procedure. A modern spectrum analyzer is able to provide a graphic display of radio signals showing not only the strength and the frequency of the signal, but it would also have the capability of displaying the waveform of the signal and demodulating any audio or other intelligence that may be present on the signal for further analysis.
A number of other radio receivers and RF accessories are also used.
- Broadband receiver- detects a wide range of signals without the need to be tuned precisely to a specific frequency. It is very helpful in recognizing that a new signal is present as well as locating the source of the signal.
- Carrier current receiver- detects signals that may be present on the AC power lines, often used for eavesdropping by using the wiring as a building-wide antenna.
- Multi-mode receivers- can tune to a specific frequency to listen to and observe a suspicious signal after it was detected by the spectrum analyzer.
- Cellular detection- is used for monitoring specific cell phone frequencies for activity.
- Wifi analysis- can detect all wifi devices in the area, identifying those that are expected to be present while alerting to any new or unauthorized devices.
- Bluetooth analysis- similar to wifi, can observe Bluetooth signals for any new or unique transmissions.
- Directional antennas- may be used help to identify the direction or location of any suspicious signals
- Remote antennas- may be placed close to or within the meeting area to provide better analysis
- Remote access receivers or analyzers- these may be needed when the only available monitoring location happens to be too far from the meeting area for good signal analysis.
Typical Set Up
Our typical set up for monitoring includes multiple spectrum analyzers that are computer controlled. One analyzer may be set to monitor specific frequency ranges that are known to be used for eavesdropping transmissions. It can alert the operator if there is any signal with strength over a certain threshold. This allows the operator to respond by performing a deeper analysis of the signal in question with other equipment and receivers.
During the course of the meetings, the analyzers and other receivers will scan through all frequency ranges, from very low frequencies (VLF) up to microwave frequencies. We ensure that all frequency bands are observed numerous times during the monitoring, noting all new or unusual transmissions.
The operator will look for:
- any transmissions that are new and were not present previously
- strong signals that may appear in the vicinity
- signals with any suspicious or unique patterns or waveforms
- any signals that contain audio or video coming from the meeting area.

Monitoring set-up may use multiple receivers and analyzers.
Computerized Analysis
Computer controlled spectrum analyzers provide valuable capabilities for understanding and identifying the radio signals that are present.
- RF sweeps that may have been recorded at a previous time (such as during a sweep earlier in the day or on previous days) can be recalled and compared with the real-time signal. Any new signals will clearly be revealed.
- Signal levels can be monitored to show the relative strength of any signal. Comparison can be made to sweeps from other locations in the facility. A transmission that is originating within a room will have a much stronger signal than one that is outside of the area.
- Demodulation of suspicious signals will often allow identification of the type of signal as well as possibly the content of the transmission. Unauthorized audio and video may be detected.
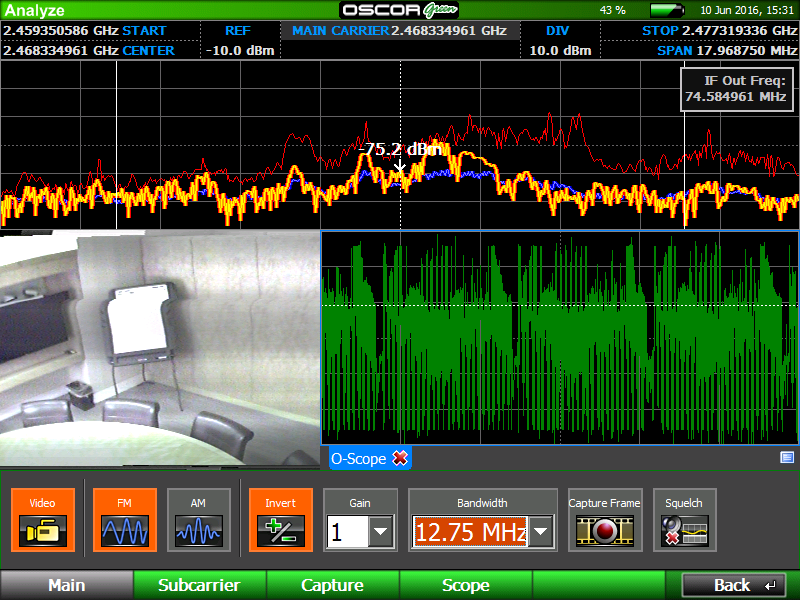
Detection and identification of a wireless camera signal.
- The history of signals over time can be viewed in what is called a waterfall This helps to reveal signals that may be intermittent, such as burst transmitters that may record audio and then transmit only periodically in an attempt to avoid detection.
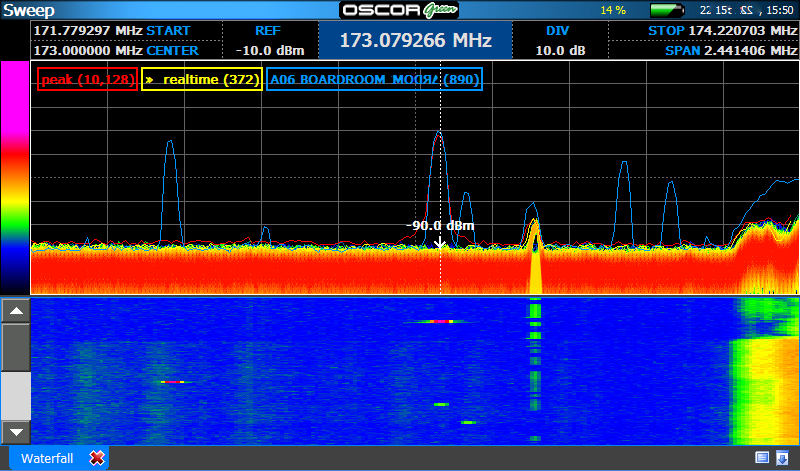
Signals may appear momentarily as bursts but can be detected over time.
In years past, radio transmissions were often analog signals and could be easily demodulated and listened to, as they were not encrypted or digitized. Today, eavesdropping transmissions may contain a variety of sounds when they are tuned in on a receiver. Some may only sound like digital noise or static, but there is still the possibility that analog signals may be used as well. Listening to a signal in real-time can allow the experienced operator to recognize the type of transmission, even if it was digital in nature. The key to determine if a signal is suspicious is to be able to observe and understand as many parameters as possible. All of the tests mentioned above help to identify signals that may pose a threat to the meeting.
In years past, radio transmissions were often analog signals and could be easily demodulated and listened to, as they were not encrypted or digitized. Today, eavesdropping transmissions may contain a variety of sounds when they are tuned in on a receiver. Some may only sound like digital noise or static, but there is still the possibility that analog signals may be used as well. Listening to a signal in real-time can allow the experienced operator to recognize the type of transmission, even if it was digital in nature. The key to determine if a signal is suspicious is to be able to observe and understand as many parameters as possible. All of the tests mentioned above help to identify signals that may pose a threat to the meeting.
Participant devices
It is well accepted that nothing today can ever be 100% secure. We need, then, to take as many steps as possible and practical to ensure as much security as is possible. This is also true for protecting meetings. Real-time monitoring as a security procedure helps to protect against threats from radio transmission threats, but there are limitations. Today, many wireless devices are frequently in use by participants of meetings. Cellular phones are one of the biggest concerns. In most corporate meetings, though, it is not practical to prevent all phones from coming into the meeting room. This poses a challenge for the security professional tasked with providing a secure environment for confidential discussions.
For a meeting to be as secure as possible, requests will need to be made for participants and staff to not bring cell phones into the room. This would certainly increase the effectiveness of real-time monitoring of cellular frequencies in particular. In most cases, though, we have to trust that anyone allowed to bring a phone into a meeting is not going to use it nefariously.
If participant devices are a big concern, there are some steps that can help to create a more secure meeting.
Other protection options:
- One option is to collect all cell phones at the door, either to keep them out of the room, or they could be placed into faraday cases or boxes within the room. Faraday boxes prevent all radio signals from getting in or out of the container. They are available in a variety of styles that may be useable in a boardroom setting.
- A walk-through cellular detection device can recognize phones that may attempt to be smuggled into a meeting. They are less obtrusive than large metal detectors and are designed to only react to cell phones or items with magnetic speakers in them, creating less of a concern for other metal objects.
- Cellular frequency detection alerting devices are available that light up when a cell signal is detected in the near vicinity. Setting up of such a device in a meeting room could help to indicate to meeting organizers if someone has either not turned off their phone or if an unauthorized device is present.
- Similar concerns also apply to laptops and other electronics including some smart watches that may require inspection.
If devices are allowed in, consider a clear policy that cell phones should be turned off. They may also act as recording devices so that is another concern.
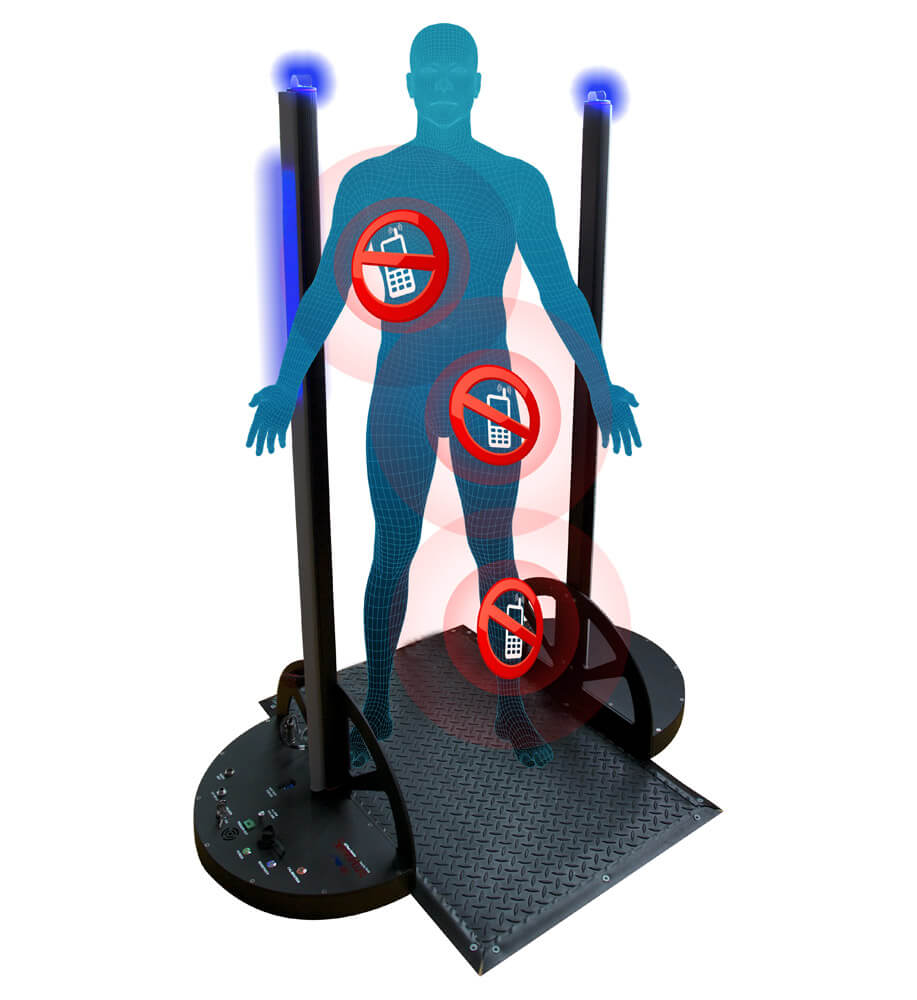

Examples of walk-through cell phone detection and a cellular phone signal blocking case.
Note that such procedures rely on clearly established policies put forth by the organization or the host of the meeting and will need compliance from the participants as well. This takes advance preparation and planning. It also may require additional staff to assist with such things as collection and tagging to ensure phones get returned to the proper owner.
Whether cell phones are removed from a meeting or allowed in, real-time monitoring will still enhance the security of the room.
Pre-existing concerns and unintended consequences
There are a number of threats that may occur from equipment or devices already installed in the meeting room. If wireless microphones are planned to be used in the meeting, they should be checked they are encrypted or at least using digital transmission. Microphones using infra-red light transmission can be a secure option.
Many facilities have analog wireless microphones already stored in the room even though they are not planned to be used for the meeting. Monitoring the frequencies of these microphones will help to ensure that none are activated during a meeting.
An example of an unintentional threat that was found came from malfunctioning AV equipment that was broadcasting an analog transmission of all the audio from the meeting. It was strong enough to be picked up by a simple receiver as far away as the company parking lot. The defective equipment was identified and removed.
Facility support staff such as AV technicians and wait-staff may have installed microphones to monitor room activities to know when certain functions were finished. These are also a threat to confidential meetings. They are often overlooked but need to be detected.
When confidentiality of a meeting is necessary, real-time signal monitoring and analysis should be an important protective measure to consider.
