Researchers in France have found that by beaming radio waves at the headset wire attached to a smart phone, they can modulate the radio waves to cause the signals in the headset wires to interpret it as voice, thus triggering the voice commands of Siri or Google Now services.
A lot of things have to be right for this to work- the smart phone must have a wired headset, the headset must have a microphone, (give them time, Bluetooth may be next), and the radio signal needs to be a powerful signal broadcast nearby with a large antenna, and you need to be oblivious to your phone suddenly reacting to unknown forces.

If you see a coworker pointing an antenna like this at your smart phone you might have cause to worry.
Voice communication can be “transposed” into other forms of modulation fairly easily. Besides radio waves, ultra-sonic waves and light waves from LED bulbs being used to transmit voice are a couple of other developments that are worth paying attention to.
If you think you are in the clear, it is still significant to be aware of such research. People are finding many ways to latch on to your information. If the researchers can do it, the criminals shouldn’t be far behind.
The researchers have a slide presentation from June, 2015, at the French security conference www.hackinparis.com available here. They include discussing various attack scenarios as well as countermeasures that could be employed by both users and manufacturers.
Attack scenarios include:
- Tracking
- Eavesdropping
- Cost abuse
- Phishing
- Malicious app trigger
- Advanced compromise
Slides from www.hackinparis.com presentation.
A recent Wired article delves into the research:
Hackers Can Silently Control Siri From 16 Feet Away
SIRI MAY BE your personal assistant. But your voice is not the only one she listens to. As a group of French researchers have discovered, Siri also helpfully obeys the orders of any hacker who talks to her—even, in some cases, one who’s silently transmitting those commands via radio from as far as 16 feet away.
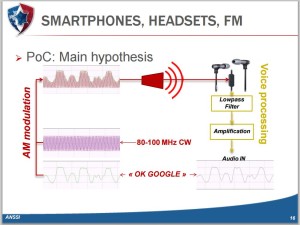
A pair of researchers at ANSSI, a French government agency devoted to information security, have shown that they can use radio waves to silently trigger voice commands on any Android phone or iPhone that has Google Now or Siri enabled, if it also has a pair of headphones with a microphone plugged into its jack. Their clever hack uses those headphones’ cord as an antenna, exploiting its wire to convert surreptitious electromagnetic waves into electrical signals that appear to the phone’s operating system to be audio coming from the user’s microphone. Without speaking a word, a hacker could use that radio attack to tell Siri or Google Now to make calls and send texts, dial the hacker’s number to turn the phone into an eavesdropping device, send the phone’s browser to a malware site, or send spam and phishing messages via email, Facebook, or Twitter.
“The possibility of inducing parasitic signals on the audio front-end of voice-command-capable devices could raise critical security impacts,” the two French researchers, José Lopes Esteves and Chaouki Kasmi, write in a paper published by the IEEE. Or as Vincent Strubel, the director of their research group at ANSSI puts it more simply, “The sky is the limit here. Everything you can do through the voice interface you can do remotely and discreetly through electromagnetic waves.”
The researchers’ work, which was first presented at the Hack in Paris conference over the summer but received little notice outside of a few French websites, uses a relatively simple collection of equipment: It generates its electromagnetic waves with a laptop running the open-source software GNU Radio, a USRP software-defined radio, an amplifier, and an antenna. In its smallest form, which the researchers say could fit inside a backpack, their setup has a range of around six and a half feet. In a more powerful form that requires larger batteries and could only practically fit inside a car or van, the researchers say they could extend the attack’s range to more than 16 feet.
The full research article by José Lopes Esteves and Chaouki Kasmi is available for purchase for a small fee from the IEEE here.
Abstract: In this paper, we exploit the principle of front-door coupling on smartphones headphone cables with specific electromagnetic waveforms. We present a smart use of intentional electromagnetic interference, resulting in finer impacts on an information system than a classical denial of service effect. As an outcome, we introduce a new silent remote voice command injection technique on modern smartphones.