Wired is almost always better than wireless when it comes to security, but you can’t take it for granted.
When sweeping a conference room recently in preparation for an important meeting, we discovered an RF vulnerability in a wired intercom headset. The AV team had set up a number of wired Clear-Com headsets for communication with each other. We were glad to see they were wired, thinking there would be no radio signal vulnerability.
Not so fast…
When comparing spectrum traces with those taken prior to the AV set up, we found a number of small spikes in the area around 60 mHz.
Further inspection revealed that the signals were coming from the headsets. Even though they were wired, they were sending analog RF along their cables. Using RF allowed multiple channels to exist within a single cable. Of course, the signals were not intended to emanate in the air, but we were able to receive and demodulate the audio from at least 20 feet away.
We found different frequencies emanating from each headset unit. Some of the frequencies we noted include: 54.6 mHz, 58.75 mHz, 60 mHz, 60.5 mHz, 61.25 mHz. The analog audio was present even when the units were inactive (when they did not have the “talk” button pressed). The units did need to be powered on for the RF audio to be detected. While the microphones are designed to mainly pick up the voice of the AV tech wearing the unit, they did transmit room audio since they were on all the time and were often left sitting on a table.
The headset model was the Clear-Com RS-601. We have not been able to test other models but would be interested if other TSCM techs may have found similar vulnerabilities.
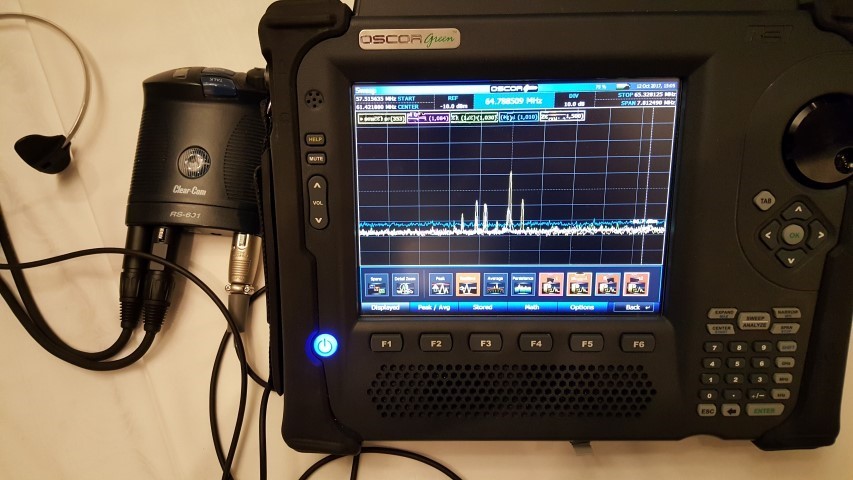
Signals detected from the Clear-Com RS-601 wired headset.
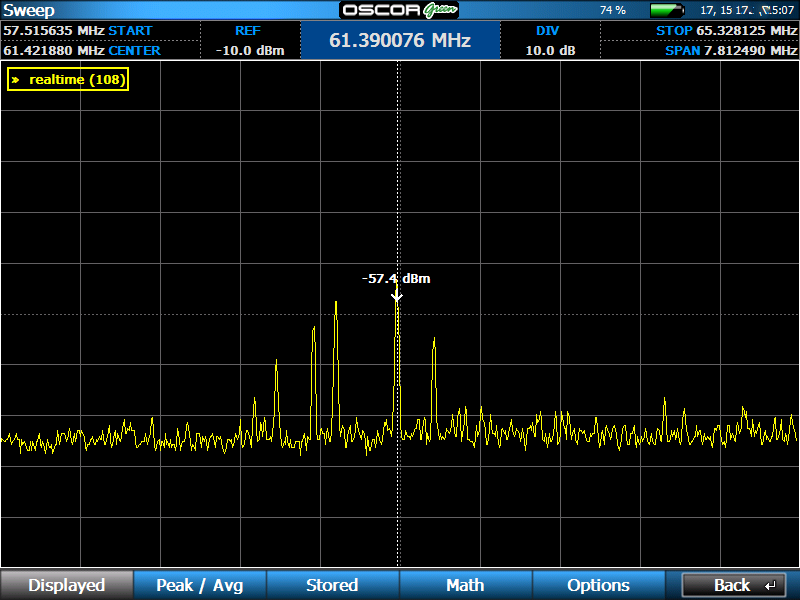
Signal trace from the Clear-Com RS-601 wired headsets.
