Earlier this year, researchers from Japan and the University of Michigan discovered that laser light could be used to send audio commands to the microphones on a number of smart home devices such as Amazon Echo, Google Home, and Apple Siri.
For those already afraid of having microphones in their homes, this could be the final straw to send Alexa to the dumpster. But how vulnerable are they, really?

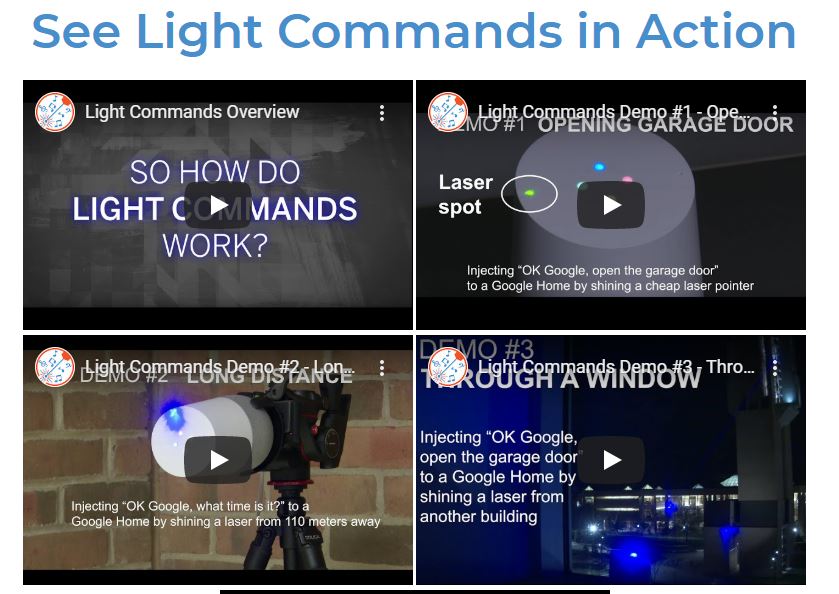
The team that did the research has developed a website that explains their research and how it functions. To make things even easier to understand, Destin Sandlin from the YouTube channel Smarter Every Day took up the task of meeting with one of the researchers, Ben Cyr, going to Best Buy and obtaining and setting up a number of smart home devices (locks, garage door opener, thermostat) and put them to the test with modulated laser beams.
Destin’s video is definitely worth watching.
Destin actually looks the microphones under a microscope to help understand and explain how they work.

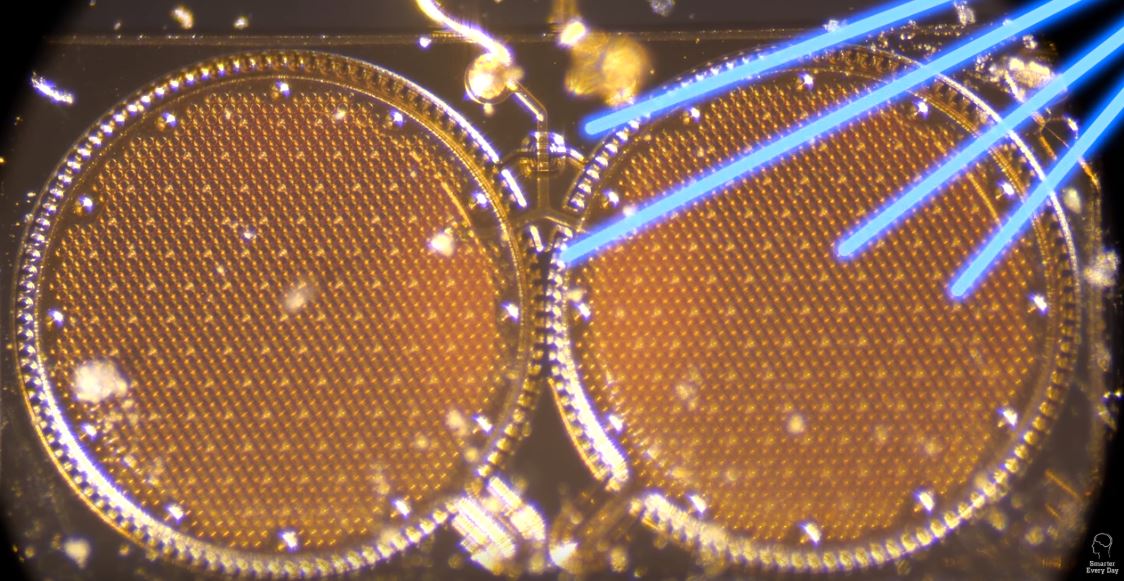
There are a number of issues that challenge the ability of lasers to reach your devices. These challenges may help the average consumer relax a bit.
- Not everyone has access to the needed laser equipment, although it is readily available to those who know where to look.
- The laser needs to be aimed directly at the microphone, so if you keep your devices away from any windows, the chance of a laser-obsessed neighbor attacking your network is slim.
- You should activate appropriate security protocols on any devices you have, such as requiring pin codes for certain functions.
- Finally, the options accessible by such hacking would only be those functions you have enabled your devices to perform. If you are seriously worried, then surely you shouldn’t use your Echo or Google Home for unlocking your doors or making extensive credit card purchases.
On the other hand, if you are in the position of managing any highly confidential corporate or government concerns, you may want to take notice of any IoT devices that may have made their way in to your offices or boardrooms and ensure that any vulnerabilities are nullified. I’m sure other risks will be revealed as technology continues to develop.
Destin explains the need to think outside the box when it comes to security:
“sometimes, when we design things with one intended purpose, sometimes they have other features that we didn’t know about. As a mechanical engineer, I would have never thought to shoot a laser at microphone. As a computer scientist or software engineer, when you design a system to be rock solid, and your code is good [secure], the moment you plug that into another system, you inherit all the vulnerabilities of that system as well.”
“You have to be thinking about your own security and safety. Configure your systems to best protect you and your family.”
The lightcommands.com website has more demonstrations they enacted.
Research paper: https://lightcommands.com/20191104-Light-Commands.pdf
Research website: https://lightcommands.com/
Destin’s channel: https://www.youtube.com/user/destinws2/