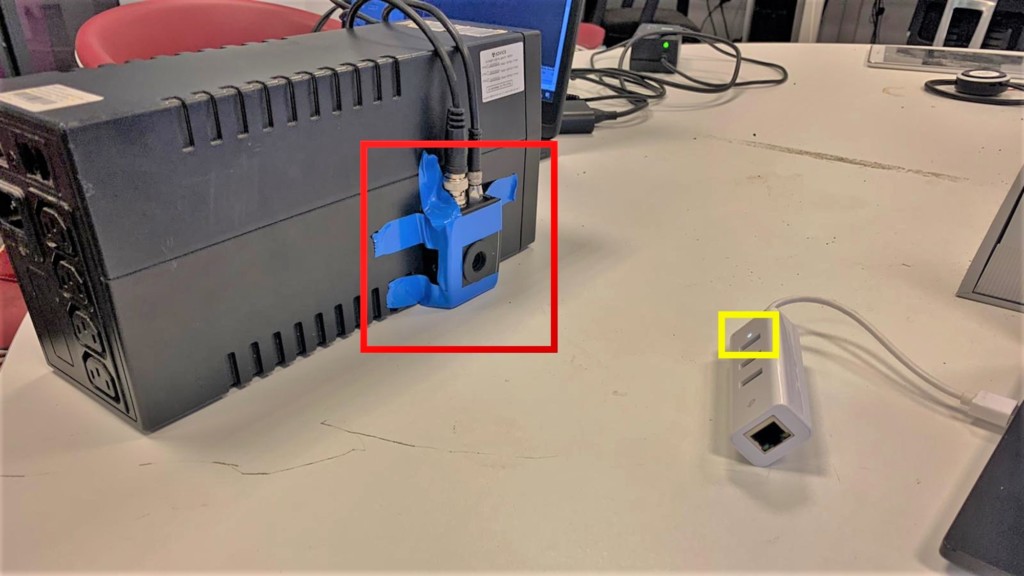
Researchers at Ben Gurion University have demonstrated a new class of TEMPEST attack for intercepting confidential information.
Their technique involves recovering sound by analyzing optical emanations from a device’s power indicator LED, specifically in the circuits providing power to various speaker systems.
It has been known for a long time that the power supplied to loud speakers will fluctuate with the volume level of the sound passing through the speakers.

Many years ago (ca 1980) I was helping to run the sound system for a church service. We knew the electric circuits in the building were in need of an upgrade, so we kept an AC power meter in the sound booth to monitor for any brown outs. Sure enough, when the preacher would make some exclamation and hit some loud spots, we would watch the meter dip from 120 volts down to as far as 90 volts and various levels in between.

That was before the days of LEDs, but now, if you turn up the volume on any number of speaker systems, you may notice slight dimming of the power LED during loud peaks. LEDs may also be fluctuating at lower sound levels as well, but ever so slightly.
Ben Nassi and his fellow researchers at Ben Gurion we able to clearly demonstrate that there is an optical correlation between the sound that is played by connected speakers and the intensity of their power indicator LED. They explain that this is due a few things: (1) the power indicator LED of various devices is connected directly to the power source, (2) the intensity of a device’s power indicator LED is correlative to the power consumption, and (3) many devices lack a dedicated means of countering this phenomenon.
Based on this, they created what they dubbed the “Glowworm Attack”. It is “an optical TEMPEST attack that can be used by eavesdroppers to recover sound by analyzing optical measurements obtained via an electro-optical sensor directed at the power indicator LED of various devices (e.g., speakers, USB hub splitters, and microcontrollers).”
Virtual meetings are now taking place regularly, which means that confidential information is being played over speakers in a multitude of homes and offices throughout the world. Each location may be vulnerable to this type of eavesdropping attack.
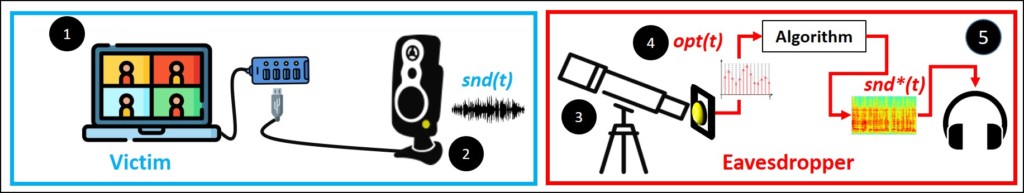
The sound from a virtual meeting (1), which is played by the connected speakers (2), creates changes in the power consumption of the power indicator LED of a connected peripheral (e.g., the speakers themselves, or a USB hub splitter). The eavesdropper directs an electro-optical sensor at the power indicator LED of a connected peripheral using a telescope (3). The optical signal is sampled from the sensor via an Analog-to-Digital Converter (4) and processed, using an algorithm to recover the acoustic signal(5).
Using their test systems, they were able to recover speech from a speaker’s power indicator LED with good intelligibility from a distance of 15 meters and with fair intelligibility from 35 meters. Examples of the intercepted audio can be heard on their website. The audio is not that clear, but it does demonstrate that the process can work in certain situations.
At this time, when so many meetings are now being held via Zoom and other video conference services, the confidential discussions and content of meetings that used to be contained within one room in the corporate headquarters, are now spread around the country and the world in executives’ homes. Each location now must consider their own security and be sure to take steps to protect their information, meetings, and conversations.
Professional electronic sweeps for executive residences should always include a consideration of both visible and infra-red light vulnerabitlities. Let us know if you have concerns or if we could be of assistance in securing your facilities and residences. We are always happy to provide phone consultation at no cost.
Read about their analysis here: nassiben.com/glowworm-attack
See their paper here: GlowwormAttack: Optical TEMPEST Sound Recovery via a Device’s Power Indicator LED