The recently discovered FaceTime bug that let iPhone users turn on the microphone of someone else’s phone is certainly a serious concern. Security directors and c-suite executives everywhere should be re-thinking their policies and consider banning or limiting cell phones being brought into board meetings and conference rooms.
The news media love a splashy story, especially if it involves a major company like Apple, so it is probably deserving of the attention it has received.
Surely you’ve heard of the FaceTime bug by now. If not, click [here]
What you probably haven’t heard about, though, is the many ways your office phone system could also allow eavesdropping both accidentally as well as intentionally.
Your phone system

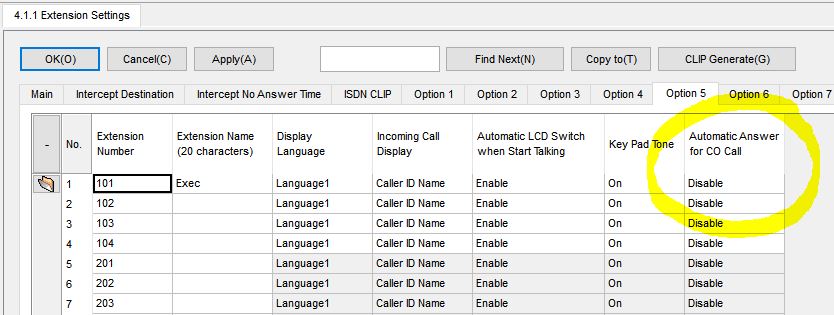
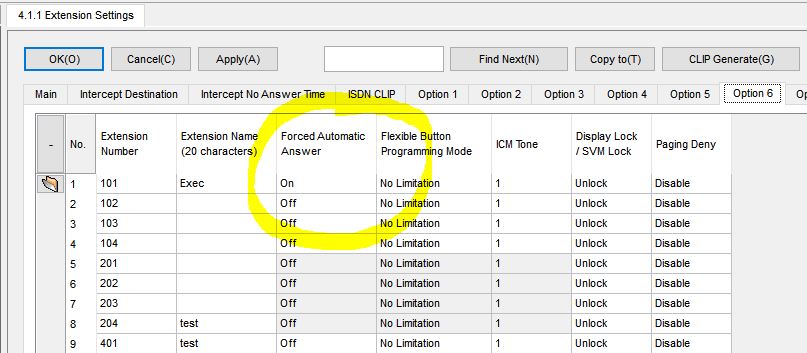
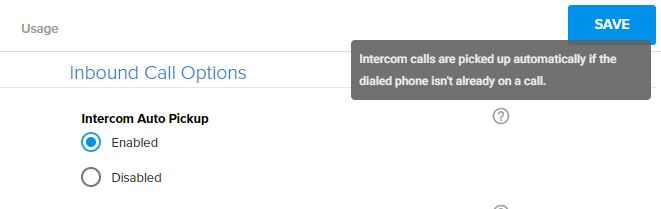
Unknown to many, is that ALL office phone systems are likely to have a “feature” that can let people eavesdrop on your conversations. A function sometimes called “auto-answer” can allow incoming calls to any phone be automatically connected and microphones turned on without the targeted user knowing or doing anything, all while leaving the phone on hook.
With this feature, any phone in the office can effectively become an eavesdropping device. Even calls from outside could be directed to an extension to be automatically answered.
PBX feature settings
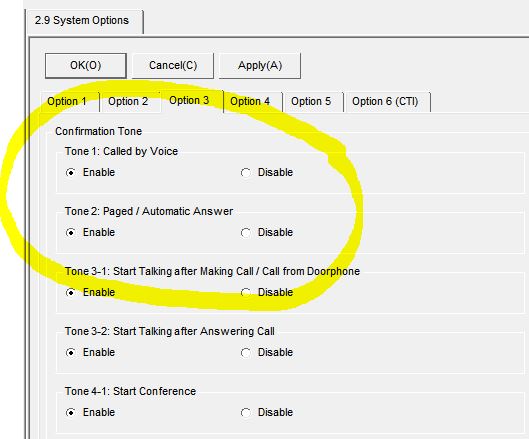
Hopefully, the default settings of such potential eavesdropping features would include some sort of warning or alert tone indication that a call has come through, but in a number of systems that we have inspected the alert or warning can be turned off. This could turn a simple office desk phone into a significant eavesdropping threat.
These features have been included in systems for many decades, and are not limited to one type of system. Analog pbx’s, digital pbx’s as well as VOIP system all have such features built in.
Some systems may only require an added digit such as * or # before or after dialing an extension in order to active the auto-answer. Other systems may require administrator programming adjustments. Such a feature might be described with different terms, depending on the manufacturer – auto-answer, intercom, or paging may refer to it, although they may have other meanings depending on the system.
Why are such features allowed in the first place?
When a bug or oversight that allows eavesdropping is found in a cell phone (eg FaceTime) or in any app or website for that matter, there is outrage and dismay publicly displayed. In plain old phone systems… not so much.
 Phone system manufacturers respond to their customers’ needs and requests and continue to add feature after feature as requests come in. A high percentage of phone systems are used by companies that with large call centers, answering thousands or tens of thousands of calls every day, so an auto-answer feature would be helpful for them. It may be for customer service, technical support, credit card processing, etc. The group of operators “standing by” using auto-answer feature could process calls more quickly and efficiently. Another type of use could be for situations such as laboratories where workers need hands-free answering capability.
Phone system manufacturers respond to their customers’ needs and requests and continue to add feature after feature as requests come in. A high percentage of phone systems are used by companies that with large call centers, answering thousands or tens of thousands of calls every day, so an auto-answer feature would be helpful for them. It may be for customer service, technical support, credit card processing, etc. The group of operators “standing by” using auto-answer feature could process calls more quickly and efficiently. Another type of use could be for situations such as laboratories where workers need hands-free answering capability.
Even though your office or your particular market may never need such a particular feature, it would still be included among the hundreds of other options, waiting to be either stumbled upon or activated by a knowledgeable technician. The manufacturers would not remove a feature just because it is not needed by a few customers.
These options are there. They may be disabled and just need to be programmed by the system administrator, or they may already be active and just require the right code to be entered when dialing. It is up to you and your system administrator to ensure your systems are not able to be misused.
Not just a PBX concern
Auto-answer is not just a feature of PBX phones, but could also be an option in other telecom or teleconference equipment.
 While performing a TSCM inspection of one corporate conference room we came across a serious vulnerability. The conference room was newly constructed with sophisticated audio and video conferencing equipment installed. The audio teleconference system was connected to an extension line on the company PBX. It was easy to determine the four digit number assigned to that extension. When we dialed that extension number from another phone, we found the teleconference equipment had it’s own auto-answer feature turned on. We were immediately connected with live two-way audio into the conference room. We could clearly hear every detail of conversations taking place in the room.
While performing a TSCM inspection of one corporate conference room we came across a serious vulnerability. The conference room was newly constructed with sophisticated audio and video conferencing equipment installed. The audio teleconference system was connected to an extension line on the company PBX. It was easy to determine the four digit number assigned to that extension. When we dialed that extension number from another phone, we found the teleconference equipment had it’s own auto-answer feature turned on. We were immediately connected with live two-way audio into the conference room. We could clearly hear every detail of conversations taking place in the room.
We continued to look further into of this vulnerability and found all phones in the facility were able to call in to the conference room. Next, we went down to the front desk. In the lobby, on the outside of the security check point, a courtesy phone sat on a table. The courtesy phone was there to allow visitors to call to the extension of the party they were visiting. We picked up the handset and dialed the number of the conference system and we were promptly connected.
To take it one step further, we realized the company used DID, or Direct Inward Dialing, in their system. This meant that they had a large block of sequential phone numbers and their phone system would direct incoming calls to specific extensions that matched the last four digits of the number dialed.
Dialing the proper telephone prefix followed by the four digits of the conference system extension from any phone (or cell phone) outside the facility would connect you directly into the conference room allowing clear eavesdropping on any conversations, board meeting, or strategy planning session that might be taking place.
Warning signs
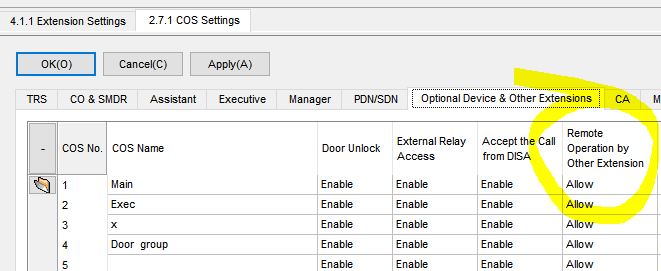
Your phone system may have alert tones built in that will beep if your phone is activated, but does that make it safe? Alert tones can often be disabled in programming (see software images below). If you do not pay close attention to your phone, you could miss the signs that you have been compromised. A malicious employee could call an auto-answer extension while an executive’s office or conference room was unoccupied, then stay on the line when the executive returns or when a meeting begins. In many conference rooms, a desk phone may reside on a side table drawing little attention from personnel in the meeting.
Other concerns
It’s not just auto-answering and voicemail that need attention. A number of other features can be misused for eavesdropping purposes.
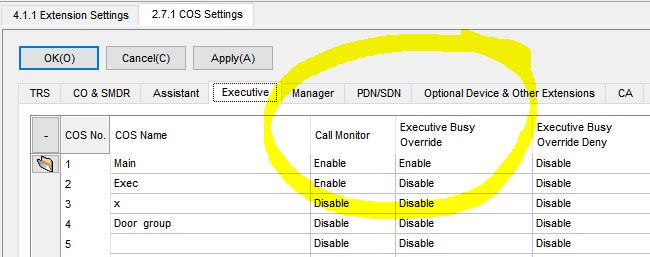
Supervisor Monitoring or “Silent Observation” is a feature designed to allow a supervisor to listen in on employees calls (often used in call centers) for “quality assurance” or training purposes. Those who can be listened to and those who can do the listening should be restricted via programming to limit the extent of their permissions.
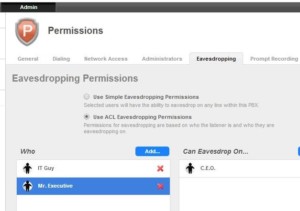
One system actually referred to the monitor option as “eavesdropping”.
Voicemail

Don’t overlook voicemail settings. Messages left on voicemail are prime targets for those trying to spy on your business. Many employees (and executives) may have never changed the default password in their mailboxes making them very vulnerable to interception.
There are numerous other voicemail features that could also leave your confidential information and business activities quite vulnerable. Many of these features are well known to hackers around the world. They do not even need a computer to hack into your system, it can be done just by dialing in and pressing the right DTMF touch-tones to navigate through your system.
Voicemail hacks are deserving of their own full article. We have resolved a number of voicemail hacking incidents going all the way back to the 1990’s. Many of the same hacks are still occurring today.
Know thy features
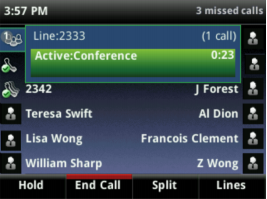
Do you know what your phone display looks like when you are in a conference call? You should pay attention if any unique or odd wording or lights shows up on your phone display.
Your phone may be telling you that someone is listening, but you may not realize it unless you know the indications. Auto-answer, conference calling, and other features may provide an indication on the desk phone when they are active, but not necessarily.
Performing an audit of the system and the administrator software is the best way to determine if any of these vulnerable features have been activated. By understanding what your systems are capable of, you will be better prepared to protect your conversations and communications.
Below are screenshots from various PBX and VOIP system programming software, showing a number of features that need to be controlled via programming: auto-answer, barge-in capability, call monitoring permission, and more. Click on image for larger view.