News sent out via mailchimp.
Interview with PwC’s cybersecurity partner Kris McConkey: “Perimeters are dissolving”
CIOs need to pull back from the perimeter and put in place security mechanisms around the data they are trying to protect, PwC’s partner in charge of cybersecurity, Kris McConkey, has advised. [via SiliconRepublic]
“Securing systems is becoming increasingly difficult and the perimeters are dissolving because we all have mobile devices and interconnectivity.
“A lot of organisations are going to be looking at how they secure data, as opposed to the systems, and will focus on keeping data encrypted but only readable by people with the right authority and access levels.”
As more small, personal devices are entering your workspace, adding TSCM to your information security program is an important step in securing your data and confidential information. Contact us to find out how we can help.





 The Santa Stake Out Kit by OpticPlanet
The Santa Stake Out Kit by OpticPlanet 

 If you see a coworker pointing an antenna like this at your smart phone you might have cause to worry.
If you see a coworker pointing an antenna like this at your smart phone you might have cause to worry.  IBM Selectric Typewriter
IBM Selectric Typewriter 
 This Instagram photo shows a listening device behind a plug socket in a wall
This Instagram photo shows a listening device behind a plug socket in a wall 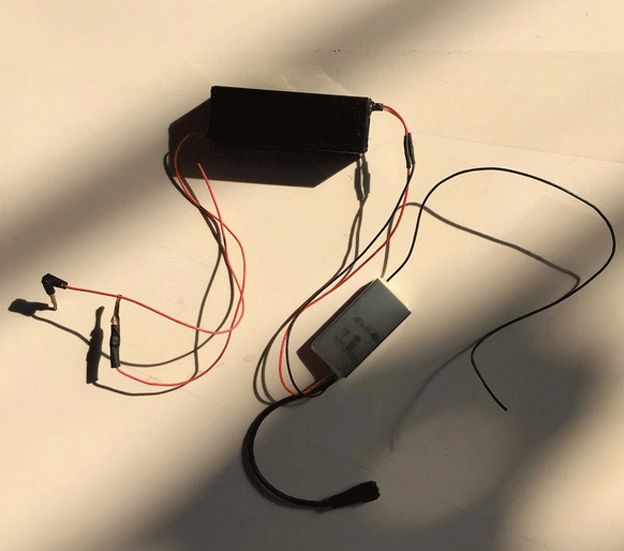 ‘There will always be surprises’ was Ai Weiwei’s caption to this photo
‘There will always be surprises’ was Ai Weiwei’s caption to this photo