New technology often results in potential threats to information security and privacy. One recent development could lead to eavesdropping transmitters that need no batteries or local power.
Wireless power
One of the challenges that eavesdroppers have faced over the years is being able to provide long lasting power to their devices. Early bugging devices often had large battery packs many times the size of the actual circuitry. The large batteries often helped the TSCM sweep team to discover the unit purely due to the size.

A recent device found by a Russian Hockey team used batteries over 10 x the size of the device itself.
Batteries have certainly become smaller and more powerful, but they still tend to run down eventually. Connecting a listening device to mains power has been the best option for long term success, but that requires extra time on site as well as advanced knowledge of the facility for the eavesdropper to be successful.


Replica of the wireless Great Seal bug, aka “The Thing”, found in the US Embassy in Moscow in 1951.
The famous Soviet bug found planted in the Great Seal in the US Embassy in Moscow was a very advanced device for its time that did not use batteries, but did require a rather sophisticated equipment at the listening post. More detail on the Great Seal bug, also known as the “Thing“, can be found here.
Battery-free cell phone
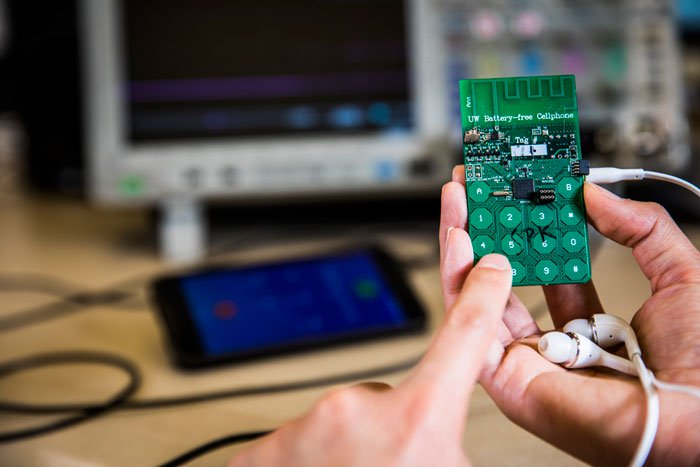
Battery-free cell phone device. [photo Mark Stone, University of Washington]
The backscatter principle is somewhat similar to the method used by the Great Seal bug. A base station must be deployed within a certain range of the radio transmitter. It will flood the area with a radio frequency (RF) signal which the unit will be able to absorb for its power.
There are other devices that use ambient RF energy as a power source, such as temperature sensors and RFID tags. Typically they are only required to transmit their signal for a short burst of data and could not be used for the continuous communication needed for a live conversation.
“You can’t say hello and wait for a minute for the phone to go to sleep and harvest enough power to keep transmitting,” said research team member Bryce Kellogg, a UW electrical engineering doctoral student. “That’s been the biggest challenge — the amount of power you can actually gather from ambient radio or light is on the order of 1 or 10 microwatts. So real-time phone operations have been really hard to achieve without developing an entirely new approach to transmitting and receiving speech.”
The researchers did find a way to make low powered analog transmissions that were able to communicate using the ambient power obtained from the backscatter. The battery-free device can run on 3.5 microwatts of power. This ambient energy would not be enough to power modern functions such as back lit screens, but it is enough to transmit and receive audio.
As a listening device threat
A common method of eavesdropping in today’s cellular rich environment is done by concealing a phone in the target area, perhaps with an external mic that can pick up room audio. This is easily accomplished with an untraceable pay-as-you-go cell phone with a simple wired headset attached. The phone, set to auto-answer, can sit unattended waiting for the eavesdropper to call for as long as the battery lasted.
With a “battery-free” device, even though it would need the base station to be placed nearby, the device itself could remain in place in a secure area for years, only to be activated when desired, by the base transmitter coming within range. The eavesdropper no longer requires access to the actual room to be spied on. It could, for example, be installed in a secure conference room during construction or perhaps during the installation of furniture or other equipment in the room.
Countermeasures
Development of such new technology highlights the need for protection of information through the use of professional TSCM firms. General sweeps using low cost equipment would not be enough to identify or locate such a transmitter. If such a device was used for eavesdropping, it could be discovered by a few methods.
Non-Linear Junction Detection would be one important test, providing the ability to recognize components on a circuit board that might be hidden in furniture or within an object being inspected.
RF analysis, though, would only be effective during times of transmission, prompting the need for real-time monitoring during confidential meetings. RF spectrum analysis should be able to detect both the base station signal as well as the response from device itself. In the example provided in the video, the base station connected to the internet to make use of Skype for the phone call. Cyber TSCM techniques would also useful in recognizing rogue devices on the network in such instances.
Maintaining the physical security of all meeting rooms and executive offices is equally important to help prevent the introduction of any eavesdropping device into the secure areas.
