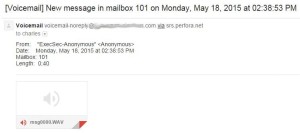
Modern phone systems, both VOIP and premise based PBX, can offer voicemail to email conversion, so that when a message is left in your voicemail box, the system will send you an email with the message recording as an attachment for you to click on to hear. That now becomes one more way for cyber hackers to lure victims into clicking on fake link containing malware.
Security researcher Graham Cluely discusses this and other recent attack methods in a article at Tripwire.com
MiniDionis: Where a Voicemail Can Lead to a Malware Attack
For just over a week, government departments, research institutes and other high-value targets have been on the sharp end of a sophisticated attack, where fake voicemails are being used to create a diversion while malware infects computer systems.
As security researchers at Palo Alto Networks’s Unit 42 division detail, it is believed the attack is being perpetrated by the same gang responsible for other malware campaigns including CrazyDuke, Seaduke, CozyDuke, MiniDuke, OnionDuke and CosmicDuke, all of which have deployed targeted attacks against governments in recent years.
Of course, whenever security firms shine a light on the activities of a malware campaign, the attackers have to change their attack frameworks or risk losing a valuable foothold inside major, government-level targets.
The use of bogus voicemails is one of the standard tricks used by the group, which involves duping victims into believing they are listening to a media file containing a voice recording of a female journalist seeking information for a news story while infecting computers with malware in the background.
Of course, a voicemail left on a regular telephone system cannot do anything like this. But through clever social engineering and targeted email campaigns, the attackers are able to dupe users into visiting websites harbouring self-extracting archives containing the voicemail recording alongside other files that download further malicious content from the web.
Researchers at Kaspersky note that in other instances the lure might be a PDF claiming to contain a report into terrorism. Often the sites harbouring the malicious code are themselves legitimate, compromised sites that are being exploited by the hackers due to sloppy security. Malware like this prefers to keep a low profile and not draw undue attention to itself because it has too much to lose if discovered. Rather than causing disruption, it would much rather hide and quietly steal and exfiltrate sensitive information via legitimate cloud services, hoping to go undetected for as long as possible.
But clearly to infect systems in the first place, it requires user involvement. Computer users either need to visit a compromised, watering hole website which can launch a drive-by download onto their PC, or social engineering needs to play its part in getting the user to click on as file or visit a web link.
If you receive emails of your voicemail messages, be sure you know how these emails should appear, and what should be in the email header, do not click on the link unless you know it is a proper voicemail message from your system.