A recent article in the NY Times caught the attention of some of our clients. It documented an architectural firm in Norcross, Georgia, that had their phone system hacked, resulting in a phone bill for $166,000 over just one weekend.
In past ExecSecurity posts we have discussed a few methods used by hackers for compromising phone systems. One aspect of the threat is actual eavesdropping and theft of information. That type of threat can be considered targeted attacks, where someone is attempting to steal information specifically from you or your company. But as mentioned in the Times article, hackers with fraud and financial gain as their motivation are hitting random targets throughout the US and the world. In such cases, the hackers do not care whose system they attack, and they will try thousands of systems looking for one that is vulnerable.
The Times article explains a common method used for this fraud. It involves causing a phone system to dial out to destinations that are set up with “toll call” services, then the company who owns the phone system gets stuck with the charges:
“Hackers sign up to lease premium-rate phone numbers, often used for sexual-chat or psychic lines, from one of dozens of web-based services that charge dialers over $1 a minute and give the lessee a cut. In the United States, premium-rate numbers are easily identified by 1-900 prefixes, and callers are informed they will be charged higher rates. But elsewhere, like in Latvia and Estonia, they can be trickier to spot. The payout to the lessees can be as high as 24 cents for every minute spent on the phone.
Hackers then break into a business’s phone system and make calls through it to their premium number, typically over a weekend, when nobody is there to notice. With high-speed computers, they can make hundreds of calls simultaneously, forwarding as many as 220 minutes’ worth of phone calls a minute to the pay line. The hacker gets a cut of the charges, typically delivered through a Western Union, MoneyGram or wire transfer.” -NY Times
Methods
Some of the common methods used include:
- Hacking into a company’s voicemail system and forcing mailboxes to activate “message notification” which normally is used to deliver your voice message to your cell phone, but tricking it into dialing the international number instead.
- Taking advantage of vulnerabilities in “auto-attendant” systems (unattended answering) that can allow the caller to dial through to an outside line where they can then dial any number but on the host company’s dime.
- Hacking the “call forwarding” feature of a phone extension and forcing incoming calls to be redirected to the toll number.
- For VOIP systems, “spoofing” the IP address of a user device is a method hackers can use to pretend to be an authorized device making the unauthorized calls.
Protection
Protection from such attacks comes down to some basic user-level measures, as well as system-level security. A number of attacks can be prevented through the use of strong passwords. This includes mailbox passwords, admin passwords, and web portal login passwords. Many of the features that can be exploited are accessible through simply dialing into a user mailbox. Users who leave their passwords at the default are the most vulnerable.
PBX system-level protections can be even more important, they can prevent user-level weaknesses from taking affect, as well as address other more technical vulnerabilities. Here are a few considerations:
- Restrict outgoing international or 1-900 calls system wide, or where ever possible.
- Restrict the voicemail system itself from dialing out, or at least from dialing international.
- Limit call forwarding capabilities, turn off remote call forwarding options.
- Restrict administrator access with secure passwords and class of service limitations (many systems allow administrator programming from individual phone sets, restrict those)
- Control who has admin access to your system. Make sure they know what they are allowed and not allowed to do without authorization.
- Monitor your bills for international calls and abnormal usage, also look for any unauthorized monthly charges.
- Monitor the “SMDR”, “station message details reporting”, that the system can print out when connected to a computer, it can show which extensions have made which phone calls.
- Consider use of “account codes” that can be assigned to those who may need international calling while blocking others.
- Set company policies regarding password usage (change regularly, or at least not using the default) and other security measures so that employees know you are serious about communications security.
Examples
One of our clients had an abnormal amount of calls going to Jamaica. By monitoring the SMDR call records, we found the calls were all originating from one maintenance phone on the wall in the boiler room. Although the phone was restricted from long distance, an employee had figured out the account code of one of the executives and passed it on to his co-workers. They were lining up at lunch time to make calls to their relatives overseas.
Another client had their voicemail system hacked- not for fraud, not for theft of information, just for harassment of the CEO. A recently fired employee knew how to navigate the voicemail options. Calling in after hours he checked the CEO’s mailbox and found it still had the default password. The employee perused the archived messages and found one from many months ago. An irate customer called in and left a ranting message cursing the CEO by name and using many expletives that cannot be printed here. The ex-employee was able to use the features of the system and “broadcast” a copy of the message to every employee in the corporation. The next morning everyone in the company came to work to find a new message in their voicemail box. The message began “You have a new message transferred from the CEO…” followed by five minutes of obscene ranting. Even though some employees may have gotten a chuckle out of it, the CEO was not amused and immediately launched an expensive investigation to figure out what had happened.
More commonly, though, clients will discover they were hacked after-the-fact, by noticing extra large charges on their bills. In some lucky cases, they may have noticed some phone lines in use during times when no one was supposed to be in the office. That would sometimes give them a chance to stop the fraud before it racked up too large of a bill. In many instances though, by the time the hacking has been discovered it is too late, the damage has been done.
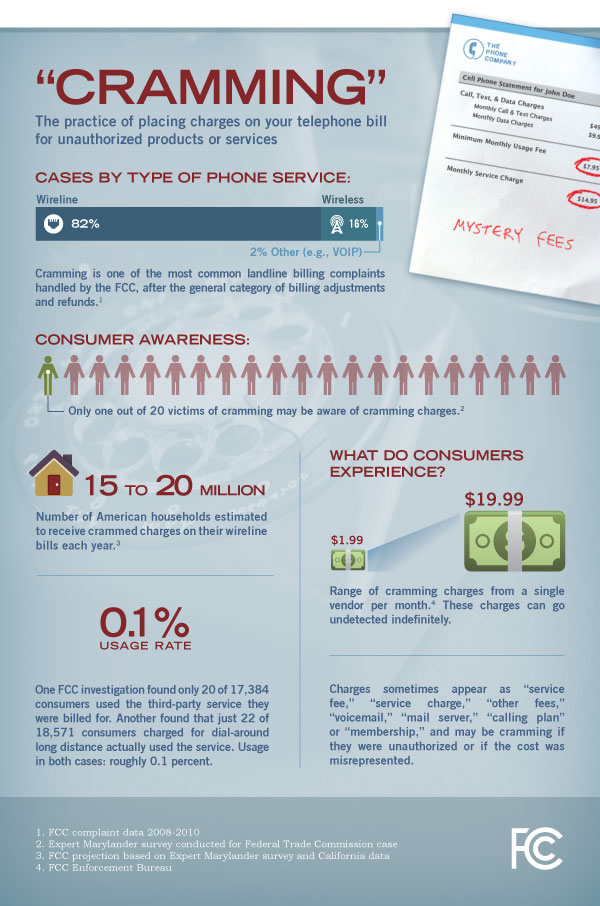
While studying your phone bill, you may also want to look for any “cramming“. That is relatively small monthly charges that could be added to the bill by the phone company from third parties for things you never asked for. They often come from calls made by employees to numbers that advertise various services, but end up getting billed to your number. We found an ex-employee at one company had obtained his own personal 800 number, billed monthly to the company and added to the main phone bill. Other charges often show up labeled as “internet service”, “voicemail”, “service fee”, or other obscure name, perhaps only for $15 or $25 per month. At this particular client we found they were paying hundreds of dollars a month for fake or unauthorized services.